Generate SSH Key using PuTTY Key Generator
OpenSSH keys are used to log in to a Linux host without a password query prompt, or to run in batch processes, for example to enable authentication from scripts.
Generate OpenSSH Key
The PuTTY Key Generator generates a key par, after which the public key is copied to the remote host.
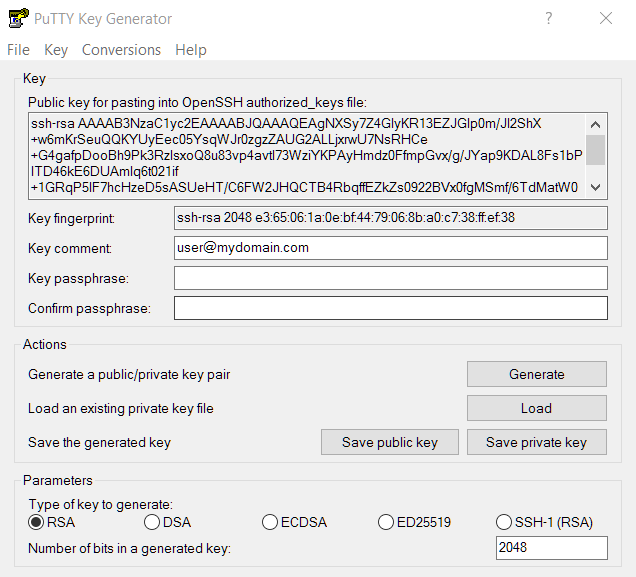
In the key comment field, your own email address can be entered, the generated private key is stored as privkey.ppk, the public key is stored as pubkey.ppk. The public key is stored on the remote host under the user’s home path in the .ssh directory in the authorized_keys file, and nothing can be changed in the copy & paste of the content.
[user@smarthost .ssh]$ ll
Total 16
drwx------ 2 user user 4096 21 Oct 2013 .
drwx------ 10 user user 4096 10 Apr 15:13 ..
-rw------- 1 user user 1124 21 Oct 2013 authorized_keysThe directory .ssh should have the right 700 and the owner must be user. This user user should serve as an example here.
PuTTY with OpenSSH Key
The host should be logged in to this one, with the IP or host name in the Session and Host Name (or IP address) section.
The path to the private key generated with PuTTY Key Generator is entered under Connection – SSH – Auth.
Auto-login username defines the user who should authenticate.
It’s done
With SSH daemon, key authentication is enabled in the configuration file /etc/ssh/sshd_config
# Authentication for user id's
AllowUsers user
# Allow key authentication
RSAAuthentication yes
PubkeyAuthentication yes
AuthorizedKeysFile .ssh/authorized_keysTip! PuTTY can be run in command-line, so scripts can be performed.
# use putty load session name
"C:\Program Files\PuTTY\putty.exe" -load smarthost.mydomain.com
# Use putty session command-line
"C:\Program Files\PuTTY\putty.exe" -i C:\Users\user\ssh-privkey.ppk user@smarthost.mydomain.complink give the possibility to use PuTTY via CLI.
plink -i C:\Users\user\ssh\privkey.ppk userd@smarthost.mydomain.comRemarks
PuTTY is free software for establishing connections via Secure Shell (SSH), Telnet, remote login or serial interfaces. PuTTY serves as a client and establishes the connection to a server. When the connection is established, the user’s identity is verified using one of the provided authentication methods. PuTTY is available for Windows and Linux.