FortiGate SSL inspection is the process of intercepting SSL/TLS encrypted Internet communication between the client and the server. Interception can be performed between the sender and the receiver and vice versa (receiver to sender). It is the same technique used in man-in-the-middle (MiTM) attacks without the consent of both entities.
FortiGate SSL Deep Inspection in Practice
When Deep FortiGate inspection is used, the FortiGate impersonates the recipient of the originating SSL session. Then decrypts and inspects the content to find threats and block them. It then re-encrypts the content and sends it to the real recipient.
In practice, this sometimes leads to unwanted blocking, especially when using self-signed SSL certificates, and the FortiGate behaves like a black box. It is also often found that the connection to the Exchange Server is denied for Outlook clients, with Outlook issuing the following error.
There is a problem with the proxy server’s security certificate.
The name on the security certificate is invalid or does not match the name mail.example.org.
Outlook cannot connect to the proxy server. (Error code 8000000).
To disable the FortiGate SSL inspection completely, you can create a clone for the Read-only Profile no-inspection under Security Profiles – SSL/SSH Inspection and configure it accordingly.
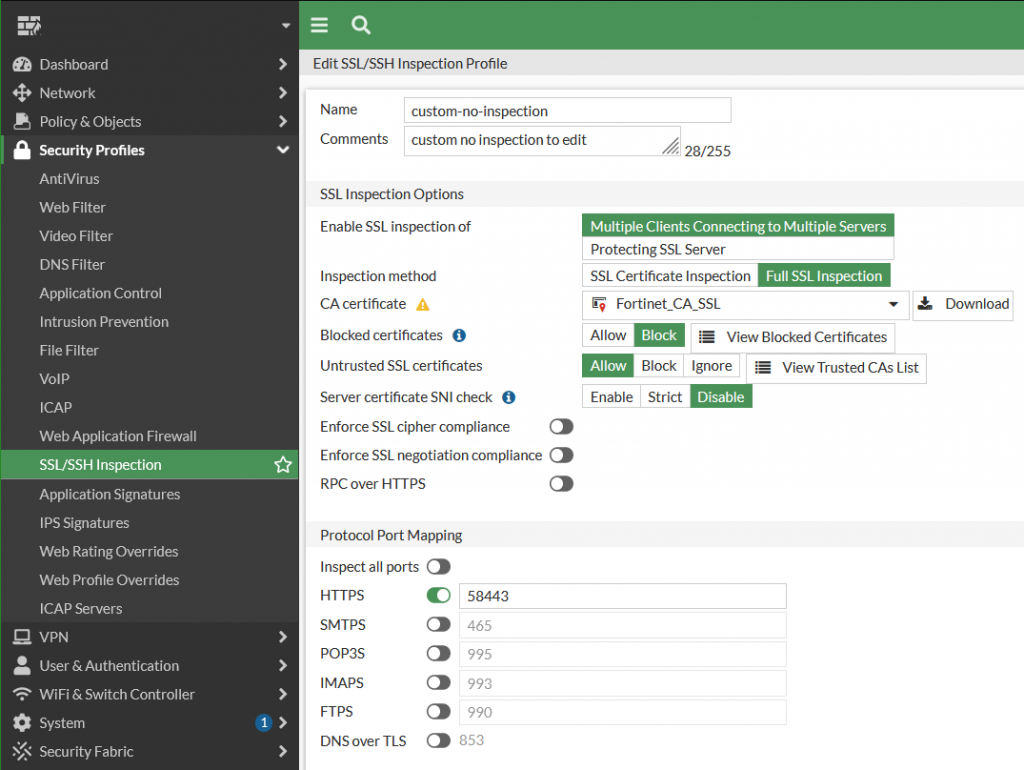
Under Protocol Port Mapping an unused port is entered for HTTPS. Which means that SSL Deep Inspection no longer takes place for port 443.
Enable the configured custom-no-inspection profile for the corresponding policy. For policies for internal and VPN connections, SSL/TLS deep inspection should not be required.