FortiGate in a site-to-site VPN configuration, the private IPv4 Subnet addresses at each scheduled end can often be the same. The problem can be solved by remapping the private IPv4 addresses using virtual IP addresses (VIP).
VIPs allow computers in its overlapping private subnets to be assigned a different range of IP addresses, and the subnets can be used transparently. The FortiGate appliance converts the VIP addresses to the original addresses. This means that if PC1 starts a session with PC2 at 10.31.101.10, FortiGate_2 the session to PC2, which actually has the IP address 10.11.101.10.
Figure shows – Finance Network VIP is 10.21.101.0/24 and the HR network has 10.31.101.0/24.
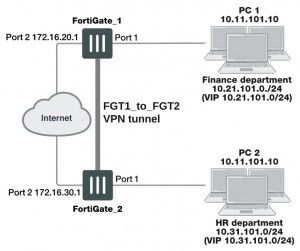
Configuration of a route-based VPN solution:
Create an IPsec Phase 1 and Phase 2, as you would normally do for a route-based VPN. This example refers to the resulting IPsec interface as IPsec_FGT1_2_FGT2.
Configuring Virtual IP (VIP) Mapping, under Policy & Objects > Virtual IPs > Create New
Create IP Pool for Subnet Remmaping under Objects – IP Pools.
Configure an outbound policy on both FortiGate, under Policy & Objects > IPv4 Policy > Create New, Leave the Policy Type on Firewall and the Policy Subtype as the address:
To configure the inbound policy:
To configure the Static Route:
Repeat this process on both FortiGate, FGT1 and FGT2, taking into account the corresponding subnets, 10.21.101.0/24 and 10.31.101.0/24.