Kopano tutorial to install on Debian 11 (Bullseye). The open source collaboration suite for e-mail and calendar server allows the greatest possible control over the data. The services cover the majority of communication needs in a organisation. A Kopano server is an alternative to the offerings that run as cloud services under the control of the providers.
Install Kopano Core |  |
Install Kopano Core
KC is installed on Debian 11 (Bullseye) in this tutorial and requires a subscription key, this serial key is available from Kopano BV for a small fee. It includes deploying Konpano Core along with the WebApp and Z-Push packages using the Apache2 web server. Depending on the speed of your internet access, provisioning takes less than 10 minutes. Let’s start by adding the KC repository, which requires your valid KC subscription key.
I prefer root through system deployments (“su -“), many also use sudo, the commands shown here are processed without sudo. Ubuntu allows become root (“sudo su -“), choose your preferred approach.
In the pre-setting, the following packages can provisioned from the Debian Standard Repository.
$ apt update
$ apt install -y gnupg2 wget apt-transport-httpsDebian 11 using of apt_auth.conf for embedding credentials needed do connect and download data from a repository.
Add the APT authentication configuration to Repository into:/etc/apt/auth.conf.d/kopano.conf
$ echo "machine download.kopano.io/supported/core:/final/Debian_11/ login serial password XXXXXXXXXXXXXXXXXXXXXXXXX" | tee /etc/apt/auth.conf.d/kopano.confNote. instead of the placeholder (“XXX”) insert your 25-digit serial key.
Add the Final Release of the Kopano Core Repository into:/etc/apt/sources.list.d/kopano.list
$ echo "deb https://download.kopano.io/supported/core:/final/Debian_11/ ./" | tee /etc/apt/sources.list.d/kopano.listNow add the PGP-Signature Release.key file to the Trusted Keys.
$ wget -O- https://serial:XXXXXXXXXXXXXXXXXXXXXXXXX@download.kopano.io/supported/core:/final/Debian_11/Release.key | tee /etc/apt/trusted.gpg.d/KopanoRelease.key > /dev/null 2>&1Note. instead of the placeholder (“XXX”) insert your 25-digit serial key.
Add the Kopano repository key into the keyring.
$ apt-key add /etc/apt/trusted.gpg.d/KopanoRelease.key
$ gpg2 --import /etc/apt/trusted.gpg.d/KopanoRelease.keyNote. you will see the message: Warning: apt-key is deprecated. Manage keyring files in trusted.gpg.d instead (see apt-key(8))..
The clue wants to tell us that the command apt-key is deprecated, but don’t worry, it’s still valid during the transition period at the time this tutorial was written. If you want to be sure, you can use this command to check if the Kopano public key are added.
$ apt-key list | grep -B 4 KopanoEnable the newly added Repository.
$ apt updateThe server is now preconfigured and processing continues with install MariaDB and the Kopano server.
$ apt install -y mariadb-server kopano-*Adding a SQL database user for the Kopano Store. the database has already been created by the installation script.
$ mysql
CREATE USER 'kopano'@'localhost' IDENTIFIED BY 'password';
GRANT ALL PRIVILEGES ON kopano.* TO 'kopano'@'localhost';
quitNote. choose a secure password instead of the placeholder.
Customize the Kopano Server
If there are no configuration files exist in/etc/kopanothe .cfg files can be found in/usr/share/doc/kopano/example-config
$ gzip -d -f --keep /usr/share/doc/kopano/example-config/*.cfg.gz & \cp /usr/share/doc/kopano/example-config/*.cfg /etc/kopanoUnpack and copy the sample configuration files (.cfg). Note. I bypass the alias ‘cp -i’ and use the non-aliased cp by prefixing it with \, if that does not work! hit unalias cp first instead of \cp.
Next edit the Kopano server configuration/etc/kopano/server.cfg
For now only the user for Kopano Admin, execution and database access will be changed.
local_admin_users = root kopano
run_as_user = kopano
run_as_group = kopano
mysql_user = kopano
mysql_password = passwordNote. the password entered for the database user in the step before.
In the final step we will start the Kopano server.
$ systemctl start kopano-serverNow of course we want to check the status of the services.
$ systemctl status kopano-*When everything worked out so far, the following output will displayed.
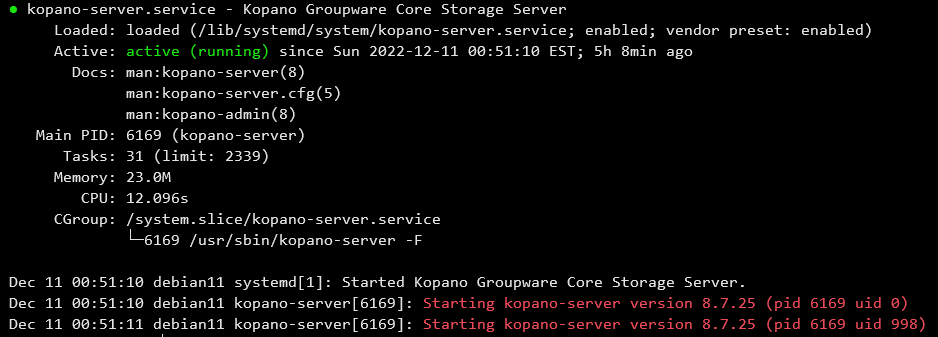
The Kopano Server configuration in this tutorial is based on the database backend. When using the database backend, nothing needs to be changed as the database user_plugin is already the default. In addition, there is the LDAP plugin (“user_plugin=ldap”) for better administration, for integration with OpenLDAP, Active Directory and Samba, which is not discussed further here.
Create an admin account to manage the Kopano Server.
$ kopano-cli --create -u kadmin --fullname "Kopano Admin" --password secure123 --email admin@example.orgInstall Kopano WebApp
The WebApp runs as front-end of the Collaboration suite, same like the most CMS they are based on the LAMP-Stack (Apache, MySQL, PHP). For Debian 11 the Apache2 web server and PHP 7.4 (“libapache2-mod-php”) from the Debian Standard Repository are installed by default.
$ apt install -y apache2 php php-common If a fresh installation of the server is chosen with Debian or Ubuntu, which is recommended for a successful KC installation, the entire LAMP-Stack (Apache, MySQL, PHP) can be easily installed with taskel. This will deploy all the packages required for the Kopano installation script to complete successfully.
The next Kopano Repository needs for WebApp to be added to:/etc/apt/sources.list.d/kopano.list
$ echo "deb https://download.kopano.io/supported/webapp:/final/Debian_11/ ./" | tee -a /etc/apt/sources.list.d/kopano.listAdd the APT authentication configuration in:/etc/apt/auth.conf.d/kopano.conf
$ echo "machine download.kopano.io/supported/webapp:/final/Debian_11/ login serial password XXXXXXXXXXXXXXXXXXXXXXXXX" | tee -a /etc/apt/auth.conf.d/kopano.confAdd the PGP-Signature Release.key to the trusted keys.
$ wget -O- https://serial:XXXXXXXXXXXXXXXXXXXXXXXXX@download.kopano.io/supported/webapp:/final/Debian_11/Release.key | tee /etc/apt/trusted.gpg.d/WebAppRelease.key > /dev/null 2>&1Instead of the placeholder (“XXX”) insert the 25-digit serial key.
Enable the newly added Repository.
$ apt updateFinally we will be ready to deploy the WebApp from the Repository.
$ apt install -y kopano-webappEnable the Kopano-WebApp site and reload the Apache2 webserver.
$ a2ensite kopano-webapp
$ systemctl reload apache2 Since secure cookies are enabled by default starting with WebApp 3.4.0, this means that the WebApp cannot be accessed without SSL certificates. This can be switched off by enabling insecure cookies in:/etc/kopano/webapp/config.php
define("SECURE_COOKIES", false);Change from true to false around line 44 to allow log-in without HTTPS.
Make sure the web server is enabled at system startup.
$ phpenmod kopano
$ systemctl enable apache2
$ systemctl reload apache2Open the URL in a browser to get the WebApp login page, i.e. http://kopano.example.org/webapp/

Another helpful post on this topic see in Kopano WebApp circle rotates endlessly in Firefox
Install Z-Push
Z-Push is an implementation of Microsoft’s ActiveSync protocol that uses wireless technology for ActiveSync-enabled devices across multiple platforms, including Apple iPhone and iPad and Android devices. With open source Z-Push, any PHP-based collaboration package can be fully synchronized with any ActiveSync compatible device.
Z-Push again provisioned from Kopano with add the Repository.
$ echo "deb https://download.kopano.io/zhub/z-push:/final/Debian_11/ ./" | tee /etc/apt/sources.list.d/z-push.listAdd the PGP-Signature Release.key to the trusted keys.
$ wget -O- https://download.kopano.io/zhub/z-push:/final/Debian_11/Release.key > /etc/apt/trusted.gpg.d/z-push.keyAdd the Z-Push repository key into the keyring.
$ apt-key add /etc/apt/trusted.gpg.d/z-push.keyEnable the newly added Repository.
$ apt updateZ-Push and Z-Push AutoDiscover can now be provisioned on the server.
$ apt install -y z-push-kopano z-push-config-apache z-push-autodiscover z-push-config-apache-autodiscoverTo activate Z-Push the web server has to be reloaded.
$ systemctl restart apache2Z-Push is now deployed and can be found at /usr/share/z-push. The configuration in/etc/z-push/z-push.conf.phpthere no changes need.
Hint! it is generally a good idea to use the complete email address as a login name, with the value of USE_FULLEMAIL_FOR_LOGIN set to true in/etc/z-push/z-push.conf.php
define('USE_FULLEMAIL_FOR_LOGIN', true);This value is also used in/etc/z-push/autodiscover.conf.php
I recommend the settingloginname_format = %uwhere the username is created with user@example.org, see the corresponding settings in/etc/kopano/server.cfg
For Multi-tenancy installations use the loginname format %u@%c.
Z-Push readiness can be verified by opening the URL in a browser.
http://kopano.example.org/Microsoft-Server-ActiveSync
If everything went well, you will be prompted to log in, use the previously created (“kadmin”) user here or, if already available, another user login, then the Z-Push ActiveSync page will appear.
Kopano and Postfix Mail Transport Agent
Kopano Core does not include its own MTA, but integrates with all established MTAs found in modern Linux distributions. Although KC supports most Linux MTAs, using Postfix is recommended.
To deliver an email to a user’s mailbox, the kopano-dagent is run. Messages are passed to kopano-dagent via the LMTP protocol. Using LMTP is the recommended deployment method as it enables Single Instance Attachment Storage.
Postfix with MySQL connection is used for this purpose, which is provisioned for the MTA as follows.
$ apt install -y postfix postfix-mysqlThe install assistant prompts you to choose the mode in which the MTA has to by run and enter a hostname for the Postfix configuration, i.e. kopano.example.org.
Add the main Postfix configuration to/etc/postfix/main.cf
myhostname = kopano.example.org
mydestination = localhost
# relayhost if relaying via a smarthost
relayhost = 172.31.245.70
mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128 172.31.245.70
virtual_alias_maps = hash:/etc/postfix/virtual
virtual_mailbox_maps = mysql:/etc/postfix/mysql-users.cf
virtual_transport = lmtp:127.0.0.1:2003
virtual_mailbox_domains = example.org
smtpd_recipient_restrictions = permit_mynetworks,
reject_non_fqdn_recipient,
reject_non_fqdn_hostname,
reject_non_fqdn_sender,
reject_unknown_client,
reject_unknown_hostname,
reject_invalid_hostname,
reject_unauth_pipelining,
reject_unauth_destination,
reject_unverified_recipient,
permitFor lookup of the recipient the password is needed again in the next step.
In addition create a file/etc/postfix/mysql-users.cf
$ echo "user = kopano
password = password
hosts = 127.0.0.1
dbname = kopano
query = SELECT value FROM objectproperty where propname = 'emailaddress' and value = '%s';" > /etc/postfix/mysql-users.cfAccording to a Kopano server in Multi-tenancy environment, I’ll use here the loginname format ‘%u@%c’ (%u Username, %c Teantname), for a system-wide unique username such as email address.
At last restrict the access rights and build the virtual Berkeley DB.
$ chmod 600 /etc/postfix/mysql-users.cf
$ touch /etc/postfix/virtual
$ postmap /etc/postfix/virtual
$ systemctl restart postfixWith incoming emails now Postfix virtual_mailbox_maps look up if the recipient (user) exists in the store using SQL query. other integrations are possible, such as interaction with LDAP, which is not covered in this tutorial.
Useful Commands
After the Kopano server is hooked up and ready to use, in the next steps we create and manage user accounts and mailbox storage using db plugin.
With a Multi-tenancy environment (only then) the following KC server setting is made bellow the MISC SETTINGS section in:/etc/kopano/server.cfg
enable_hosted_kopano = true
storename_format = %u
loginname_format = %u@%cIn a Multi-tenancy installation, first we will become an organization with the domain they create their company space.
$ kopano-admin --create-company -s -I company.orgCreate a new user account for the organization.
$ kopano-admin -c kate@company.org -p password -e kate@company.org -f 'Kate Middleton' -a1Here will be set administrator level for user with -a1.
Do not forget to create a mailbox store for new created user.
$ kopano-cli --create-store -u kate@company.orgNow check whether the new user actually exists with list users, users will now logging in using the e-mail address as the username.
$ kopano-admin -l
User list for company.org(2):
Username Fullname Homeserver
-----------------------------------------------------------
SYSTEM SYSTEM Unknown
kate@company.org Kate MiddletonFor help hitkopano-admin --helpalso further detailed information view the man page or hitman kopano-adminin your terminal shell.
Let’s Encrypt SSL/TLS Certificate Authority (CA)
The deployment of Let’s Encrypt and it’s ACME implementation with Certbot is done quickly with just only two commands.
$ apt -y install certbot python3-certbot-apache
$ certbot --apache -d kopano.example.orgConclusion
The Kopano server is now complete with all functions that can be used by the desktop and mobile clients. A further variety of applications and plugins can be provisioned, the infrastructure integration for active directory or samba and OpenLDAP may be further steps.



