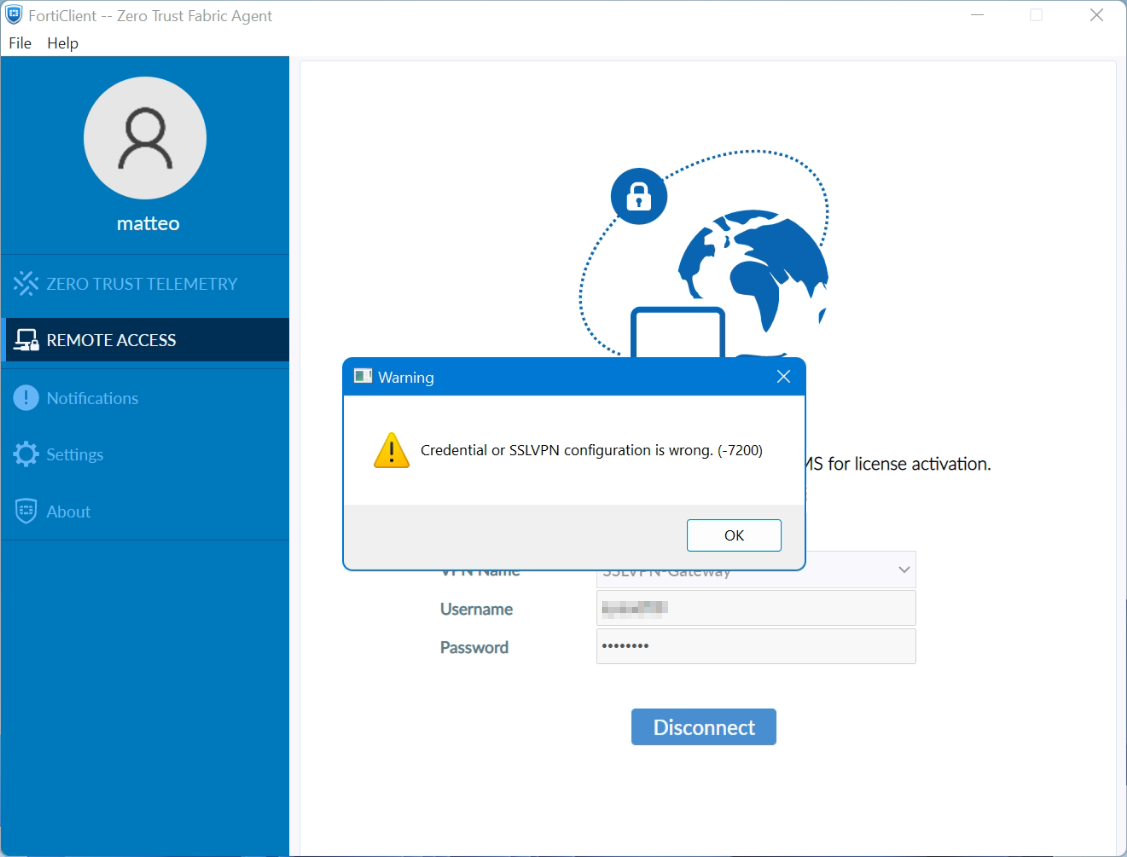
FortiClient on Windows 11 shows the Warning: Credential or SSLVPN configuration is wrong. (-7200)
FortiClient SSL-VPN connects successfully on Windows 10 but not on Windows 11. An article by the staff was posted in the fortinet community they describes a potential cause for why SSL-VPN connections may fail on Windows 11 yet work correctly on Windows 10.
SSL-VPN tunnel-mode connections via FortiClient fail at 48% on Windows 11, it shows the warning: Credential or SSLVPN configuration is wrong (-7200). We remember, tunnel-mode connections was working fine on Windows 10.
Users are unable to authenticate if they are in a User Group that is configured in an SSL-VPN Authentication/Portal Mapping (known as authentication-rule in the CLI), but they can successfully authenticate when using the All Other Users/Groups catch-all authentication rule.
Windows 11 is uses TLS 1.3 by default for outbound TLS connections, whereas Windows 10 appears to use TLS 1.2 by default.
The cipher setting is set to high by default. This setting specifically designates the acceptable key-strength of the encryption cipher being used to ≥ 168 bits.
If TLS-AES-256-GCM-SHA384 is removed from the list, Windows 11/FortiClient will still be able to establish a TLS 1.3 connection using one of the alternative TLS Cipher Suites available.
Windows 11 may be unable to connect to the SSL-VPN if the ciphersuite setting on the FortiGate has been modified to remove TLS-AES-256-GCM-SHA384, and an SSL-VPN authentication-rule has been created for a given User Group that has the cipher setting set to high (which it is by default).
The solution can be determined as follows by running the command in the FortiGate CLI to solve the issue. First of all, show the current SSL-VPN settings used on the FortiGate appliance:
show vpn ssl settingsThen use unset to make the cipher suite according to windows 11:
config vpn ssl settings
unset ciphersuite
endOr set the cipher suite with the append command:
config vpn ssl settings
append ciphersuite TLS-AES-256-GCM-SHA384
endNote see Microsoft learn about TLS Cipher Suites in Windows 11