How to Check File Integrity
SHA256 hash values provide information about the integrity of a file, for example, they can protect against manipulated programs. Unixoid operating systems already have the checksum tools like sha256sum on-board. Windows 10 includes a cmdlet in PowerShell with which the checksums can be quickly checked.
What are checksums
To ensure the integrity of a file, checksums (MD5, SHA256, SHA512, …) are created. A checksum is formed over all bytes of a file (the byte values are multiplied by different numbers according to certain rules.) The value calculated in this way uniquely identifies the file content. If you re-generate the checksum at a later time (or on another computer) and compare it with the first one, you can see whether the file has been modified. This principle is also often used to check whether a file transfer has taken place without errors.
Check SHA256 hash checksum
Checking the hash signature is particularly suitable for downloads. An ISO image or archive file can be checked for integrity and authenticity after downloading. The manufacturers and developers publish signatures with which an image of integrity and authenticity can be compared by means of the SHA256 hash or MD5 hash value. So that the unchanged origin and originality can be ensured without this being the case with a man-in-the-middle attack.
PowerShell Get-FileApply Hash
This example checks the Linux Mint 20 ISO image that was previously downloaded. To verify the integrity of an ISO image, the SHA256 sum is generated and compared, with the SHA256 hash in the sha256sum file.txt,which is also downloaded.
The files linuxmint-20-cinnamon-64bit.iso and sha256sum.txt are copied to a folder, then you open PowerShell and switch to the folder where the cmdlet Get-FileHash is now executed.
Get-FileHash linuxmint-20-cinnamon-64bit.iso -Algorithm SHA256
Algorithm Hash Path
--------- ---- ----
SHA256 2F6AE466EC9B7C6255E997B82F162AE88BFE640A8DF16D3E2F495B6281120AF9 C:\linuxmint-20-cinnamon-64bitThe SHA256 hash of the ISO image is generated.
Then open the previously downloaded file sha256sum.txt which contains the hash. Checksum hash are often referred to as checksum or file fingerprint.
Get-Content sha256sum.txt
2f6ae466ec9b7c6255e997b82f162ae88bfe640a8df16d3e2f495b6281120af9 *linuxmint-20-cinnamon-64bit.isoAs you can see, sha256sum.txt contains the hash string in lowercase, but the hash is calculated by Get-FileHash in uppercase, so that we can then use the hash for the comparison, we convert it from sha256sum.txt to an uppercase string with ToUpper().
$text="2f6ae466ec9b7c6255e997b82f162ae88bfe640a8df16d3e2f495b6281120af9".ToUpper()
Write-Host $text
2F6AE466EC9B7C6255E997B82F162AE88BFE640A8DF16D3E2F495B6281120AF9The hash string of Get-Content sha256sum.txt is inserted between the quotation marks in $text.
Get-FileHash Parameter -Algorithm
algorithm specifies the cryptographic hash function to use to calculate the hash value from the contents of the specified file or stream. The acceptable values for this parameter are:
- SHA1
- SHA256
- SHA384
- SHA512
- MD5
If no value is specified or the parameter is omitted, the default value is SHA256.
For security reasons, MD5 and SHA1, which are no longer considered secure, and they should only be used for simple change verification, but not to generate hash values for files that need to be protected from attack or tampering.
The procedure can then look like the following in a PowerShell script for this example.
$text="2f6ae466ec9b7c6255e997b82f162ae88bfe640a8df16d3e2f495b6281120af9".ToUpper()
$hash=(Get-FileHash linuxmint-20-cinnamon-64bit.iso -Algorithm SHA256 | Select-Object -Property Hash | ft -HideTableHeaders)
Write-Host $text
Write-Host $hashThe comparison of both hash values with the following line in PowerShell.
[string]$text -eq [string]$hashHash Calculate and Compare
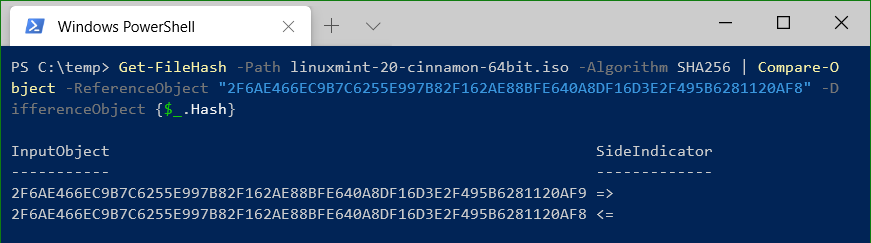
The following script calculates the hash value and compares it with Compare-Object and the fingerprint from the signature.
Get-FileHash -Path linuxmint-20-cinnamon-64bit.iso -Algorithm SHA256 | Compare-Object -ReferenceObject "2F6AE466EC9B7C6255E997B82F162AE88BFE640A8DF16D3E2F495B6281120AF9" -DifferenceObject {$_.Hash}If the checksums match, no output appears.
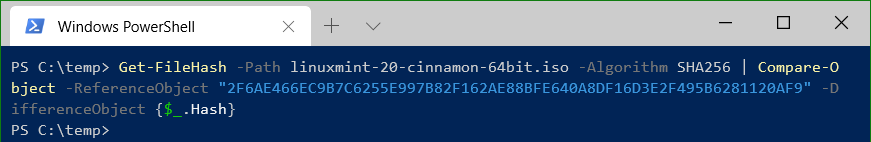
If the hash values does not match, then both objects are displayed.