Ping a Range of IP Addresses using Windows PowerShell
Ping an IP range in the PowerShell, you can instantly determine if the IP addresses within a subnet are available and reachable on a windows machine. It also shows you which IPs are connected to a device und which device is currently online.
Launch start ![]() or press the Windowskey, then type
or press the Windowskey, then type powershell on the keyboard, select powershell app in the chooser.
Out from the opened PowerShell run the two lines one after each other with use copy and paste.
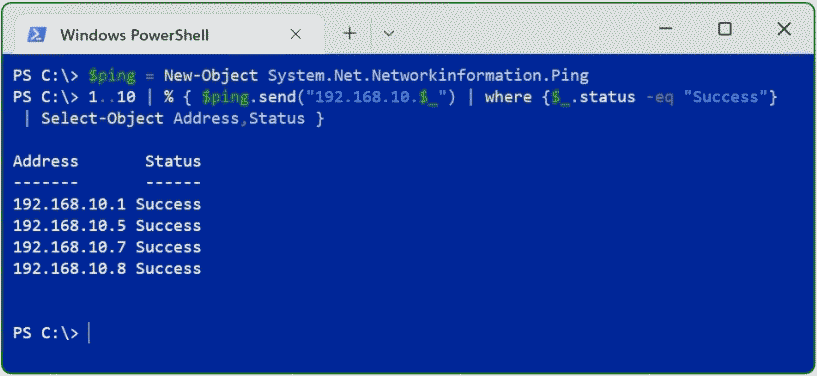
$ping = New-Object System.Net.Networkinformation.Ping
1..10 | % { $ping.send("192.168.10.$_") | where {$_.status -eq "Success"} | Select-Object Address,Status }IP range “1..10” Change the start (1) or end (10) to the IP range you want to ping on the network. Note that the last octet figure can’t exceed 255.
The command sends Ping to an IP range as ICMP echo request messages in the PowerShell. To all IPv4 addresses in this range and wait for echo replies. The output will look similar this.
If you get truncated output then use the command bellow.
10..100 | % { $ping.send("192.168.10.$_") | where {$_.status -eq "Success"} | Select-Object -Property Address,Status | Format-Table -AutoSize }Remarks Ping Range in PowerShell
This PowerShell class provides functionality similar to the Ping.exe command line tool. The Ping class sends an Internet Control Message Protocol (ICMP) echo request message to a remote computer and wait for an ICMP echo reply message from that computer.
Conclusion
This post shows how you can easily ping scan IP subnet in PowerShell. Without using additional tools that have to be installed first.


