SSH Tunnel to Linux VNC Servers
VNC connections are considered unsafe because they are not encrypted. VNC sessions can be encrypted with OpenSSH, where traffic is routed through a secure SSH tunnel and is protected.
The SSH tunnel requires user login and the VNC port. The client command runs in the Linux CLI as follows:
$ ssh -L 5901:127.0.0.1:5901 -N -f -l USER 10.127.55.77If user USER replaces it with the actual user name, a password is prompted to run the tunnel. Please note that this is the password for the SSH login, the user login to the VNC can ideally be the same UID, then the password is the same. The port that needs to be tunneled is 5901. The command runs on the computer of the VNC viewer. Registration takes place as usual:
login as: USER
USER@10.127.55.77's password:
Last login: Thu Oct 11 07:59:26 2018 from 10.127.55.70
[USER@fedora ~]$With the VNC viewer, the virtual desktop session can now be run to the loopback address:
vncviewer 127.0.0.1:5901Note: The options must be enabled for the OpenSSH Server in the /etc/ssh/sshd_config configuration file.
AllowTcpForwarding yes
X11Forwarding yesSSH tunnel on Windows to vnC server
On Windows, an SSH tunnel to the VNC server can be opened using PuTTY or KiTTY, tunneling via the loopback interface and port 5901.
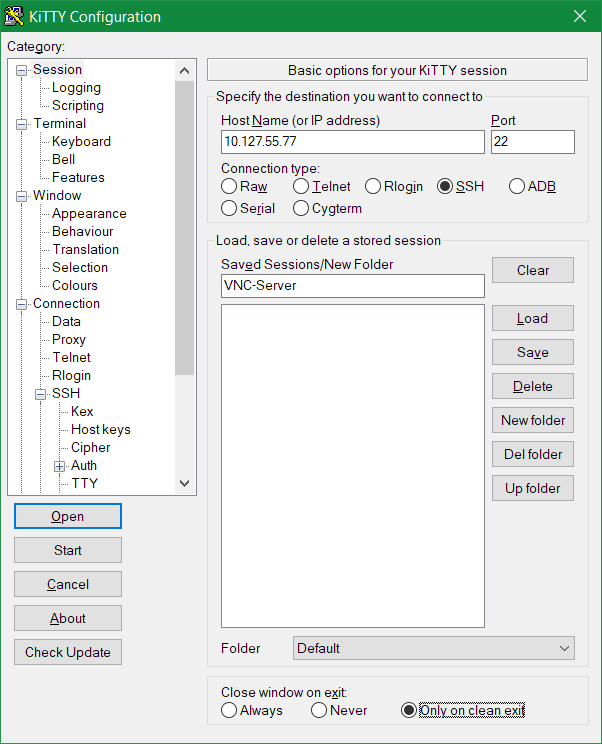
Under the Category, Connection – SSH – Tunnels, at Source Port 5901 is entered, Destination is 127.0.0.1:5901, then by clicking on Add the tunnel is added.
Clicking on Open starts the tunnel by logging in to the VNC host.
The secure SSH connection to the VNC server can now be initialized. Remote Host registers the loopback address 127.0.0.1 with port 5901 in the TightVNC viewer: 127.0.0.1:5901
After registration, Connection provides information about the current connection by clicking on the icon in the menu bar.