To check the .NET Framework version with PowerShell on Windows 10 and Windows 11, follow these steps.
In this tutorial you show how to check the installed .NET Framework version by using PowerShell. Here we go, hit the
Check .NET Framework version in PowerShell
Paste the following line into PowerShell and hit the Enter key.
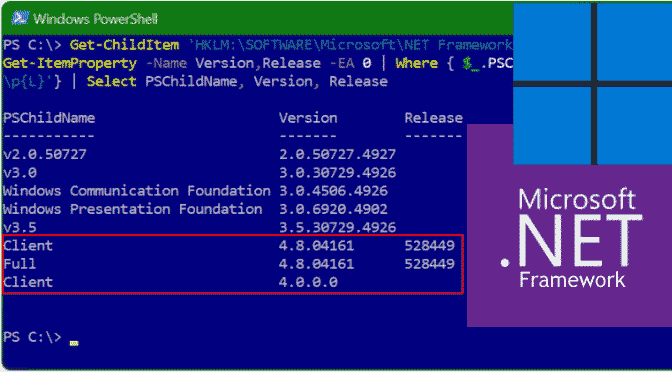
Get-ChildItem 'HKLM:\SOFTWARE\Microsoft\NET Framework Setup\NDP' -Recurse | Get-ItemProperty -Name Version,Release -EA 0 | Where { $_.PSChildName -match '^(?!S)\p{L}'} | Select PSChildName, Version, ReleaseIf you ran the command above, PowerShell will return the information for both the client and the full version of .NET Framework installed on Windows 10 or if you are already using Windows 11.
Enable .NET Framework 3.5 by using PowerShell
For a Windows Server 2012 or later installation that isn’t connected to the Internet, you can use PowerShell to add .NET Framework 3.5 and provide access to the \sources\sxs folder on the installation media. The \sources\sxs folder can be copied to network share (for example, \network\share\sxs) to make it easily accessible to multiple computers. The target computer account DOMAIN\SERVERNAME$ must have at least read access to the network share.
Start Windows PowerShell in the Administrator Command Prompt by typing.
powershellTo install .NET Framework 3.5 from installation media located on a network share, use the following command.
Install-WindowsFeature Net-Framework-Core -source \network\share\sxsTo verify installation, run the following command.
Get-WindowsFeatureUse .NET classes with PowerShell
The PowerShell itself was developed on the basis of the .NET Framework 2.0. In addition, all objects within PowerShell are based on the .NET object model and the classes from the .NET framework can also be used with basic functions, i.e. without the help of other tools.
This means that PowerShell users have access to an enormous function library that can be used to cover many use cases. However, in-depth knowledge of the .NET framework is absolutely necessary. This article shows basic access.
Static properties and methods can thus be called directly. There is no need to instantiate the class, i.e. to create an object.