Suppress ServerSignature and ServerTokens on Apache and Nginx HTTP-Server
There are numerous ways websites can be exposed to security threats. Information in the ServerSignature and ServerTokens is an increased risk for systems and can be used against them.
The ServerSignature and ServerTokens of Apache und NGINX HTTP-Server provides important information about the web server with the extensions and the operating system. For an Apache server on Debian GNU/Linux, the Apache version number and operating system information is displayed in the HTTP server header signature.
$ wget --server-response --spider http://www.foo.com/index.php
Spider mode enabled. Check if remote file exists.
--2020-12-12 14:41:06-- http://www.foo.com/index.php
Resolving www.foo.com (www.foo.com)... 198.51.100.2
Connecting to www.foo.com (www.foo.com)|198.51.100.2|:80... connected.
HTTP request sent, awaiting response...
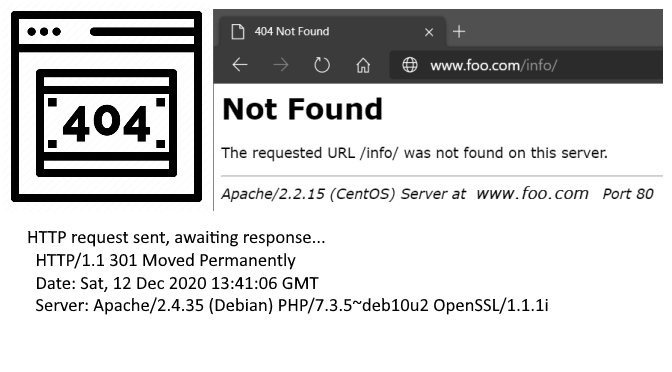
HTTP/1.1 301 Moved Permanently
Date: Sat, 12 Dec 2020 13:41:06 GMT
Server: Apache/2.4.35 (Debian) PHP/7.3.5~deb10u2 OpenSSL/1.1.1i
Location: https://www.foo.com/index.php
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=iso-8859-1
Location: https://www.foo.com/index.php following
Spider mode enabled. Check if remote file exists
...This information displayed in the HTTP server header at line 9 and provides information about the web server version number and the PHP version, the OpenSSL version for Transport Layer Security and the operating system.
Suppress Apache HTTP-ServerSignature
The HTTP-ServerSignatures can contain sensitive information about the software versions running on the web server. If a page is not found on the server, the server sends the client an error page and the page appears in the browser.
HTTP/1.1 404 Not Found
A dead link is returned to the browser with the HTTP status code 404, and further information about the web server and version used are also disclosed.
It is recommended that the ServerSignature and ServerTokens be deactivated if the system is to be protected from open threats. This tutorial shows how to disable and suppress the serversignature.
Disable Apache HTTP-ServerSignature on Debian GNU/Linux
Under Debian 10 and newer the ServerSignature is configured in the file security.conf.
$ vi /etc/apache2/conf-available/security.confThe default setting on Debian 10 or newer also on Ubuntu for ServerSignature is On and ServerTokens is Full.
ServerTokens Prod ServerSignature Off
You can suppress ServerSignature and ServerTokens as follows.
ServerTokens Prod
ServerSignature OffApply change the Apache web server configuration.
$ systemctl restart apache2.serviceDisable Apache HTTP ServerSignature for RedHat Linux
On RedHat the serversignature is changed in the Apache configuration httpd.conf file.
$ vi /etc/httpd/conf/httpd.conf
...
ServerTokens Prod
ServerSignature Off
..Apply changes of the HTTP server signature for RedHat Linux.
$ systemctl restart httpd.serviceAfter disable the ServerSignature, it is no longer displayed in the HTTP server header output. The modification can be checked using wget or here.
$ wget --server-response --spider http://www.foo.com/index.php
Spider mode enabled. Check if remote file exists.
--2020-12-12 15:15:33-- http://www.foo.com/index.php
Resolving www.foo.com (www.foo.com)... 198.51.100.2
Connecting to www.foo.com (www.foo.com)|198.51.100.2|:80... connected.
HTTP request sent, awaiting response...
HTTP/1.1 301 Moved Permanently
Date: Sat, 12 Dec 2020 14:15:33 GMT
Server: Apache
Location: https://www.foo.com/index.php
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=iso-8859-1
Location: https://www.foo.com/index.php following
Spider mode enabled. Check if remote file exists.
...The deactivation of the serversignature can also be achieved with .htaccess, this is created in the Docroot if it does not already exist.
htaccess is only using by Apache web server.
$ echo -e "ServerTokens Prod\nServerSignature Off" >> .htaccessDisable PHP-Version HTTP Server Header
The output of the PHP version number is deactivated in Debian 10 or newer by expose_php off in the php.ini file.
$ vi /etc/php/7.3/apache2/php.ini
...
expose_php = Off
..For Rocky Linux (RedHat) the PHP version header is suppress in /etc/php.ini file by expose_php directive.
$ vi /etc/php.ini
...
expose_php = Off
..Apache HTTP-Response-Header
The Apache ServerTokens directive has the following possible values that are sent to clients when the specific value is set.
ServerTokens Prod
The Server send (i.e.): Server: Apache
ServerTokens Major
The Server send (i.e.): Server: Apache/2
ServerTokens Minor
The Server send (i.e.): Server: Apache/2.0
ServerTokens Minimal
The Server send (i.e.): Server: Apache/2.0.41
ServerTokens OS
The Server send (i.e.): Server: Apache/2.0.41 (Unix)
ServerTokens Full
The Server send (i.e.): Apache/2.4.37 (Debian) PHP/7.3.5~deb10u2 OpenSSL/1.1.1
This setting applies to the entire server and cannot be enabled or disabled on a virtualhost basis.
NGINX HTTP server_tokens OFF
The file nginx.conf must be modify for Nginx web server.
$ vi /etc/nginx/nginx.conf
http {
...
server_tokens off;
...Apply changes let disappear the Nginx serversignature.
$ systemctl restart nginx.serviceNow the server header will only indicate Nginx with no version number.