Identify SSL/TLS Cipher used by an Browser HTTPS Secure Connection
When making a connection using HTTPS, either SSL or TLS will be used to encrypt the information being sent to and from the server. This connection are encrypted by Cipher algorithm and makes it very difficult for a third party to read the data packets between you received in the browser. The information is encrypted using a Cipher or encryption key, the type of Cipher used depends on the Cipher Suite installed and the preferences of the server.
This post describes how to find the Cipher used by an HTTPS browser connection, by using Microsoft Edge, Google Chrome or Mozilla Firefox, to show the current cipher suite and certificate information.
Find the Cipher in Microsoft Edge Browser
- Launch Microsoft Edge.
- Enter the URL you wish to check in the browser.
- Click on the three-dots on the top-right (Alt+F) in the browser.
- Select More tools > Developer tools > Security (Ctrl+Shift+I).
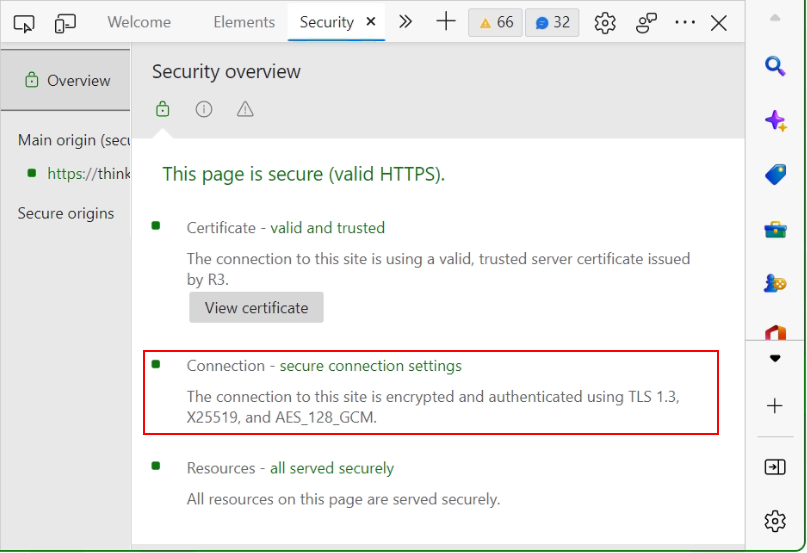
Find the Cipher in Google Chrome Browser
- Launch Google Chrome.
- Enter the URL you wish to check in the browser.
- Click on the three-dots on the top-right (Alt+F) in the browser.
- Select More tools > Developer tools > Security (Ctrl+Shift+I).
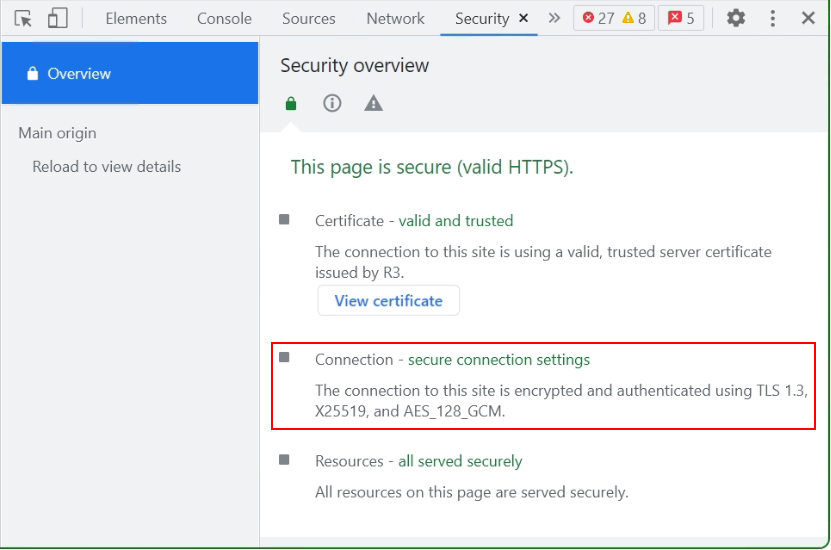
How to find the Cipher in Firefox Browser
- Launch Firefox.
- Enter the URL you wish to check in the browser.
- In the address bar, click the icon to the left of the URL.
- Now click on Connection secure > More Information.
Now see the Cipher connection in the Browser.
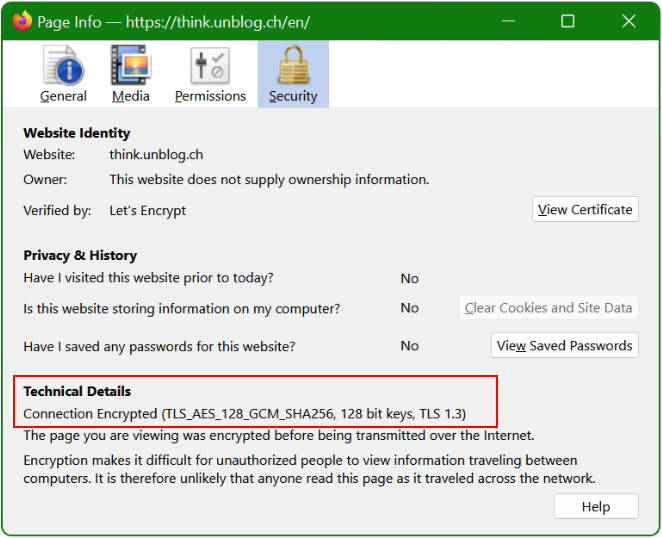
How to find Cipher using OpenSSL
If you are using a Linux machine and the OpenSSL library is available on the preferred system, you can run the command in the example below.
openssl s_client -connect think.unblog.ch:443 | find "Cipher"The next command causes openssl to produce the Cipher connection without using a browser.
$ openssl s_client -verify_quiet -brief think.unblog.ch:443
depth=2 C = US, O = Internet Security Research Group, CN = ISRG Root X1
CONNECTION ESTABLISHED
Cipher Protocol version: TLSv1.3
Ciphersuite: TLS_AES_256_GCM_SHA384
Peer certificate: CN = unblog.ch
Hash used: SHA256
Signature type: RSA-PSS
Server Temp Key: X25519, 253 bitsWhat is Cipher Suite?
SSL is standard technology for securing an internet connection by encrypting data sent between a website and a browser (or between two servers). It prevents hackers from seeing or stealing any information transferred, including personal or financial data.
A cipher suite is a set of cryptographic algorithms. The schannel SSP implementation of the TLS/SSL protocols use algorithms from a cipher suite to create keys and encrypt information. A cipher suite specifies one algorithm for each of the following tasks: Key exchange. Cipher Browser connection.