How to set up Postfix to check email SPF record
In addition to an A Record, MX and PTR record, mail servers (MTA) also require an SPF record in DNS.
What are SPF Records
Sender Policy Framework (SPF) is a method of sender authentication. Like DKIM, SPF is a TXT data set of DNS that is designed to help prevent email spoofing and identify it as legitimate when delivering your own emails. Also, the e-mail is not to be prevented from ending up in the junk e-mail folder at the recipient. If a domain is abused by e-mail spoofing, the emails are likely to end up in the recipient’s spam folder.
The SPF record specifies which hosts or IP addresses are allowed to send e-mail on behalf of a domain. You should only allow your own mail server or your ISP server to send e-mail for this domain.
Create SPF record in DNS
An SPF record is a DNS record that is added to a domain’s DNS zone. The SPF record in a DNS zone can look like this:
IN TXT "v=spf1 a mx "all"When managing the domain of an Internet web hosting provider, this may look something like this.
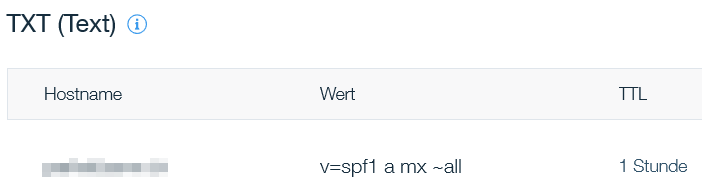
- TXT indicates that this is a TXT record.
- v=spf1 indicates that this is an SPF record and the SPF record version is SPF1.
- mx means that all hosts listed in the MX records are allowed to send emails for the domain, all other hosts are not allowed.
- -all Fail – servers that aren’t listed in the SPF record are not authorized to send email (not compliant emails will be rejected).
- ~all Softfail – If the email is received from a server that isn’t listed, the email will be marked as a soft fail (emails will be accepted but marked).
- +all It is strongly recommend not to use this option, this tag allows any server to send email from this domain.
- include – An additional SPF request for the domain specified in the include statement that contains the IP address of the sender.
To verify that the SPF record is resolved on the public Internet, the dig utility on the Linux host should be used for querying as follows:
dig domain.com TXT +short
"v=spf1 a mx "all"On a Windows computer, nslookup can be run in a command prompt (cmd), the change may be delayed depending on the TTL:
C:\> nslookup -type=txt domain.comIn the PowerShell, Resolve-DnsName is used with the following command:
PS C:\> Resolve DnsName Name domain.com -type TXT | ft -a
Name Type TTL Section Strings
---- ---- --- ------- -------
domain.com TXT 3485 Answer sv=spf1 a mx
Online SPF validators such as mxtoolbox can also be used to check which hosts are allowed to send the emails of their own domain.
Postfix SPF Policy Agent pypolicyd-spf
For our Postfix SMTP server, we still need an instruction to check the SPF record of incoming emails to detect fake emails. To do this, install the pypolicyd-spf package from the EPEL repository as root:
yum install epel-release
yum install policyd-spfThen add a user for Policyd SPF:
adduser -U -M -s /bin/false policyd-spf
Postfix Master Configuration
Now edit the postfix master configuration file master.cf:
vi /etc/postfix/master.cf
policyd-spf unix - n n - 0 spawn
user=policyd-spf argv=/usr/libexec/postfix/policyd-spf
Add the lines at the end of the file master.cf, instructing Postfix to start the SPF policy demon. Policyd-SPF runs as a user policyd-spf.
Policyd SPF should not run in a chroot environment.
Save and close the file.
Postfix Main Configuration
Next, edit the postfix main configuration file main.cf:
vi /etc/postfix/main.cf
policyd spf_time_limit = 3600
smtpd_recipient_restrictions =
permit_mynetworks,
permit_sasl_authenticated,
reject_unauth_destination,
check_policy_service unix:private/policyd-spf,
PermitThe line with policyd-spf should come to reject_unauth_destination to stand. Save the file and then restart Postfix:
systemctl restart postfixCheck SPF record of received email
The next time an email is received from your domain with an SPF record, the SPF check results are displayed in the raw email header. The following header indicates that the sender of the email was sent by an authorized host.
Received-SPF: Pass (mailfrom) identity=mailfrom;Postfix logs the SPF check results in maillog with syslog as follows.
Jul 19 07:10:38 mailhub policyd-spf[24382]: Pass; identity=helo; client-ip=12.34.56.78; helo=mail77-192.srv2.com; envelope-from=return@news.domain.com; receiver=max.muster@domain.com