How to Get Windows User SID
For system administrators, querying information about the environment and configuration is an everyday job. One of these information is the Security Identifier (SID), which is used by Windows to identify users and groups. User names on a network can be duplicated, so that there is no conflict, each user is assigned a unique SID.
When assowing user rights, Windows uses the SID defined for that purpose. A SID is roughly similar to a Globally Unique Identifier (GUID) that each object in Windows owns. However, SIDs receive only security-relevate objects, because the SID is used for authentication of authenticity.
This SID identifies the user across the network. Even if the user’s name is changed, the SID persists, the user on the network is deleted and his SID is unchanged.
Structure of my SID
S-1-5-21–4147432549-3588766049-1627529166-1001
The SID (Security Identifier) tokens have the following meanings:
| S | It is a SID |
| 1 | Revision |
| 5 | Identifier Authority |
| 18 | System profiles |
| 19 | Localservice |
| 20 | Networkservice |
| 21 | User profile |
| 4147432549-3588766049-1627529166 | Domain ID, Computer ID |
| 1001 | User ID (RID) |
Table with SID of system accounts
Query SID of all user accounts
If you want to get the SID of all user accounts. You can do so with the following command in a Command Prompt Win+Rcmd
wmic useraccount get sid,nameAll SIDs and user names are output.
C:\>wmic useraccount get sid,name
Name SID
Administrator
S-1-5-21-4147432549-3588766049-1627529166-500
DefaultAccount
S-1-5-21-4147432549-3588766049-1627529166-503
John
S-1-5-21-4147432549-3588766049-1627529166-1001
Guest
S-1-5-21-4147432549-3588766049-1627529166-501Here are the SIDs of the local accounts. For a query in a network domain, there may be some more.
Computer and domain SIDs consist of a base SID and a relative ID (RID) appended to the base SID. If the computer belongs to a domain, another SID comes into play. The computer still has its own computer SID and local accounts and groups. But is also a member of a domain and therefore has a SID that represents the computer account in that domain. The SID of a computer account consists of the SID of the administrator account, minus the RID, which is omitted last 3 bit or 4 bit (500).
Query to get my own user SID
If a user’s SID is to be specifically queried, such as his own user SID, this can be done with the following command.
wmic useraccount where name='%username%' get name,sidIf you want to know another user’s SID, you can specify a user instead of %username%, e.g., john.
The following command detects the SID of the user who is currently logged on in an AD domain.
wmic useraccount where (name='%username%' and domain='%userdomain%') get domain,name,sidIn the opposite way, it is also possible to query the user name of a SID.
wmic useraccount where sid='S-1-5-21-4147432549-3588766049-1627529166-1001' get nameGet user SID in the PowerShell
In the PowerShell, the get user SID command looks like this.
[wmi] "win32_userAccount.Domain='$env:UserDomain',Name='$env:UserName'"The user name and SID of the user logged on to the company domain is output.
PS C:\>[wmi] "win32_userAccount.Domain='$env:UserDomain',Name='$env:UserName'"
AccountType : 512
Caption: company-john
Domain : company
SID : S-1-5-21-4147432549-3588766049-1627529166-1001
FullName : john smith
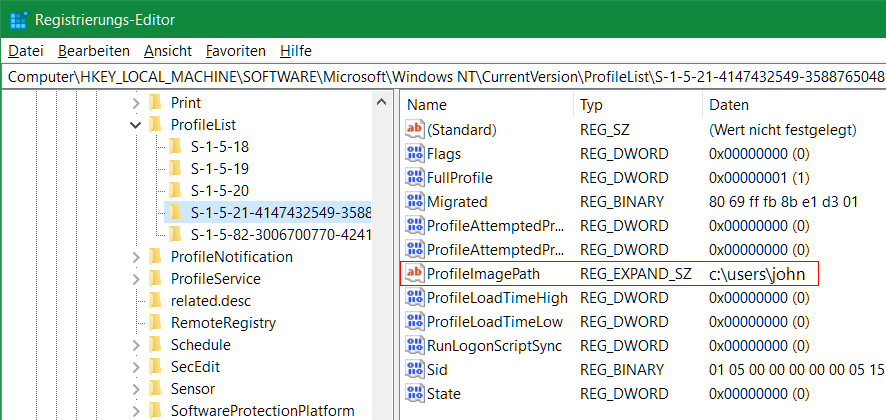
Name : johnFor example, you can use the user SID to find the ProfileImagePath for the user profile in the registry in order to make repairs or adjustments. The user SID is also used as an ObjectID in SQL tables to identify and authorize users from Active Directory in an application, such as Dynamics AX.