After initializing an OPNsense as a virtual machine, access to Web GUI via WAN is denied. With a newly deployed OPNsense virtual machine on a hypervisor. Such as a VMware ESXi host, the Web GUI cannot yet be reached directly from the internet.
Assign interfaces and Set interface IP address
In order to be able to access the OPNsense GUI via WAN, as with every new installation. You have to call up and follow the wizard with the option 1) Assign interfaces and 2) Set interface IP address. This to lay the basis for the OPNsense. With the interfaces and the IP configuration for the WAN and LAN interface.
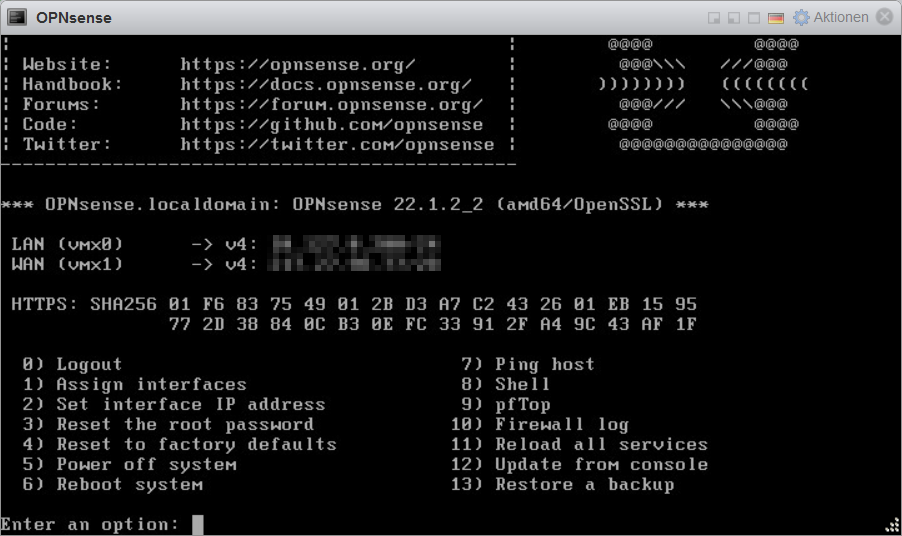
Next step, the firewall packet filter (pf) must be disabled in the vSphere console of the virtual machine.
Disable packet filter
With option 8) Shell execute the command pfctl -d:
root@OPNsense:~ # pfctl -d
pf disabledNow the Web GUI can be opened via the WAN IP address in a browser.
Permanent access to OPNsense GUI via WAN
In order to enable permanent access to OPNsense GUI via WAN. A new rule must be created under Firewall – Rules – WAN with pass in to this firewall.
IMPORTANT! Do not explicitly select a gateway, the gateway must be default. The gateway previously created in the console with Set interface IP address is only required for the WAN interface configuration.
After the default gateway has been selected, the OPNsense must be restarted. With the command reboot, or with option 6 from the OPNsense console menu.
Note! after each restart, the packet-filter (pf) firewall is enabled, the command pfctl -e to enable the pf-firewall is not required. At the beginning, when setting up the OPNsense do not add a second gateway.
It should not go unmentioned here that the OPNsense is adequately protected against misuse and brute force attacks. It is recommended to only allow the WAN rule for access to the OPNsense web GUI from known sources. Also a user-defined port number for the web GUI can be defined under System – Settings – Administration for TCP Port in order to override the default setting (80 for HTTP, 443 for HTTPS). For this purpose, 2FA TOTP authentication with Google Authenticator is also possible, this in the post here.
The next relevant post might also be helpful How to Setup OPNsense as a Virtual Machine.