This tutorial describes how to start an SSH terminal session under Windows, open the connection from the KeePass Manager, the known password Safe, with using OpenSSH and the Windows Terminal. Prerequisite is that OpenSSH is installed on Windows, from Apps & Features – Optional Features. The Windows Terminal can be found in the Microsoft Store.
The new Windows Terminal has evolved and achieves the parity to be measured with modern terminals of other operating systems such as the GNOME Terminal. Not only is it free, it can also be seen with the well-known terminal tools on Windows, such as PuTTY and KiTTY.
Windows Terminal is located under this path for batch processing.
%LOCALAPPDATA%\Microsoft\WindowsApps\wt.exe
Here from KeePass via the field URL with the “cmd://” argument.
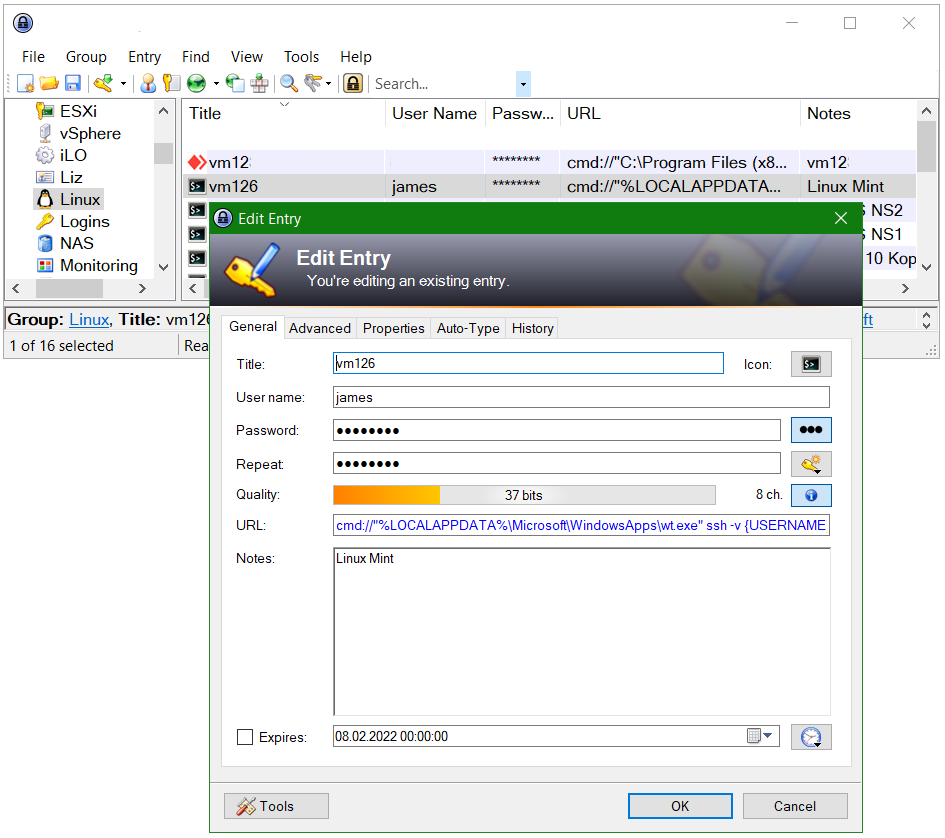
For the entry in KeePass, add the following line into the URL field.
cmd://"%LOCALAPPDATA%\Microsoft\WindowsApps\wt.exe" ssh -v {USERNAME}@{TITLE}
From the “Title” field, the hostname is passed in {TITLE}, from “User name” the user-ID is passed in {USERNAME}. If a different port is used for SSH add the port e.g. -p 60622
Click OK to close and save the entry. A double-click on the entry in the URL column opens the Windows Terminal.
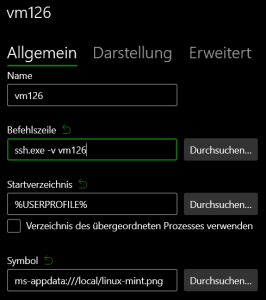
The host entry is added in the Windows Terminal settings (Ctrl+,) with add new profile.
Keys generated with ssh-keyen can be used SSH sessions without entering a password and even more securely.
SSH session using Windows KeePass and Windows Terminal
To do this, create the folder.ssh under the home path %USERPROFILE%, in which private and public keys are stored. Then creating the file config to assign hostname to the appropriate key.
Host vm126
HostName 10.10.0.11
User james
IdentityFile ~/.ssh/id_rsa
ServerAliveInterval 60The public key (id_rsa.pub) is stored on the remote host at ~/.ssh/authorized_keys
the
configfile offers many options for configuring ssh targets so that they can be started easily in the Windows Terminal CLI.

