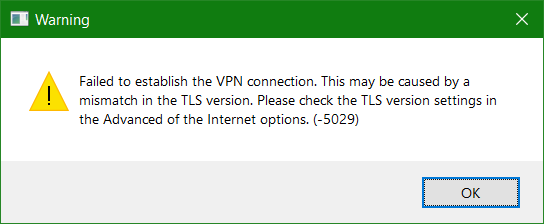
FortiClient Failed to establish the VPN connection by TLS. This may be caused by a mismatch in the TLS version. Please check the TLS version settings in the Advanced of the Internet options. (-5029)
Using FortiClient to establish an SSL-VPN connection to the FortiGate can output a warning message.
Symptom
Cause

The now outdated cryptographic protocol TLS 1.0 is no longer enabled by default as of FortiOS 6.0. It is recommended to use at least TLS 1.1 (Cipher Suites) for authentication and data encryption. We are currently on TLS 1.3 which has been approved by the IETF (Internet Engineering Task Force).
Solution
If you want to continue use older FortiClient VPN connection that are only ready for use later with TLS 1.2 or higher may if planned client migration via update rollout, TLS 1.0 can be activated on the FortiGate.
This measure should only be used temporarily, TLS 1.0 is outdated and is no longer considered secure.
Check current TLS settings
Check the current TLS setting from the FortiGate VPN Console with CLI Command:
FG60E # get vpn ssl settings | grep tls
tlsv1-0 : disable
tlsv1-1 : enable
tlsv1-2 : enable
dtls-hello-timeout : 10
dtls-tunnel : enableActivate in the CLI the Cipher Suite TLS 1.0.
config vpn ssl settings
set tlsv1-0 enableHow to enable TLS 1.0 on Windows
The TLS version 1.0 in the Microsoft Windows snap-in (inetcpl) Internet Options can also be activate.

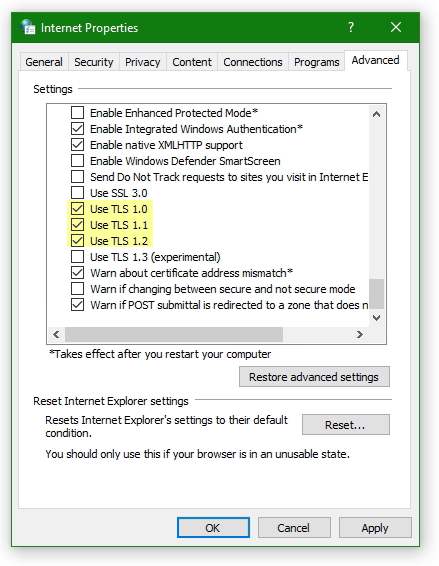
Hit the key Win+R and enter inetcpl.cpl
In the opened Internet Options window Internet Properties click to Advanced tab and click Use TLS Version 1.0 to enable it.
Troubleshooting MTU size in VPN connections
According to FortiClient VPN TLS using on older Windows versions, or with routers with PPPoE Internet connection, errors when establishing SSL-VPN connections can be eliminated as follows.
It appears the FortiClient error message:
Unable to establish the VPN connection. The VPN server may be unreachable (-5)
Check MTU size using netsh in command prompt
To do this, check the MTU size of the network interfaces with the following command from an open command prompt
netsh interface ipv4 show subinterfaceThe output might look something like this:
C:\> netsh interface ipv4 show subinterface
MTU Medienerkennungsstatus Bytes eingehend Bytes ausgehend Schnittstelle
------ --------------- --------- --------- -------------
1500 5 0 0 Ethernet
1500 1 598892209 19487894 WiFi
1500 5 0 0 Mobilfunk
1500 1 5248 144442 VMware Network Adapter VMnet1
1500 5 0 0 LAN-Verbindung* 1
1500 1 0 134436 VMware Network Adapter VMnet8
1500 5 0 0 LAN-Verbindung* 5
4294967295 1 0 67869 Loopback Pseudo-Interface 1
1500 5 0 0 Bluetooth-Netzwerkverbindung
1500 5 0 0 Ethernet 3Check the MTU size and adjust to 1400 if necessary. In a command prompt opened as an administrator, with running netsh.
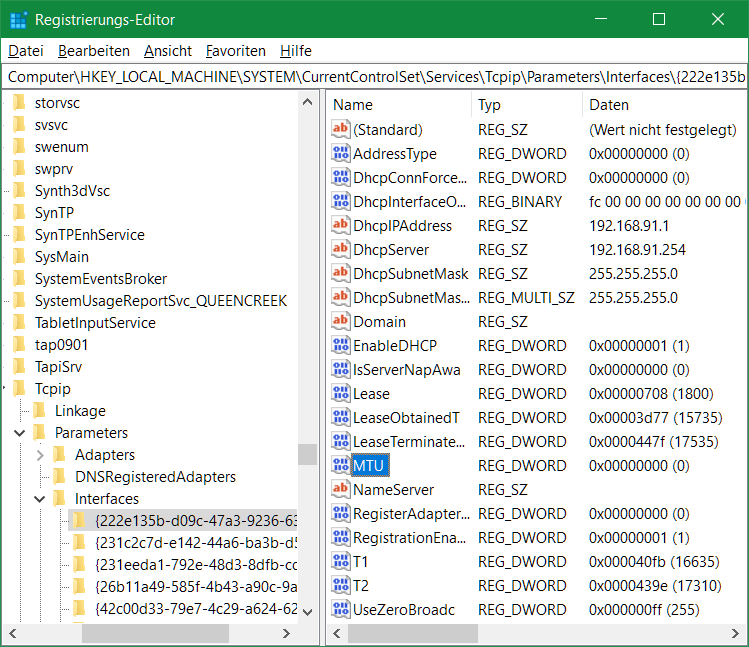
netsh interface ip4 set subinterface Ethernet mtu=1400 store=persistentAlternatively, call Regedit and navigate to the following key.
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfacesunder the appropriate interface with the appropriate IP address, here {222e135b-d09c-47a3-9236-63a041a02ea6} change the key MTU with the value 578 hexadecimal.
After restarting the computer, the SSL-VPN connection can be established.