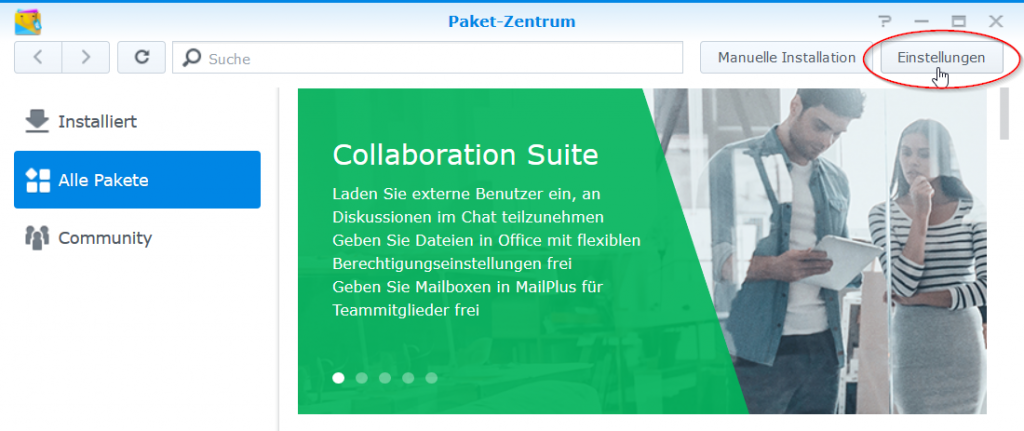
Easy authentication with SSH keys using ssh-keygen on Linux, Windows and macOS, secure connection to SSH host without a password. This tutorial shows how to create a private key and store the corresponding public key on the Web Server.
How to use SSH keygen
SSH keys eliminate the need to enter passwords when connecting via SSH. Especially for the administration of several accounts, this can bring a lot of time savings. The following describes how to creating SSH keys with ssh-keygen on Linux, Windows and macOS. To do this, open a terminal and ran the following command.
$ ssh-keygen -t rsa -b 4096Generate SSH key with ssh-keygen
ssh-keygen now asks in which file the SSH key should be stored, preferably create a new unique file. The default is that the key is stored in the default file (id_rsa), which is confusing, and the folder “.ssh” is also hidden.
$ ssh-keygen -t rsa -b 4096
Generating public/private rsa key pair.
Enter file in which to save the key (/home/mike/.ssh/id_rsa): my-key
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in my-key.
Your public key has been saved in my-key.pub.
The key fingerprint is:
SHA256:7oBofs25Wz2b03V2+5daXFUAq8ClijSfSjUog/3sVwo mike@thinkpad
The key's randomart image is:
+---[RSA 4096]----+
| . .....|
| o . . o . .|
|. + + o + . .|
| * = + . . .|
| E + S . .|
| + + + . o =|
| o +o+.o o. . =+|
| o ..++ .+. .o.|
| .. oo. o. .. +|
+---- SHA256 -----+A SSH key is created by ssh-keygen using the RSA cryptosystem with a length of 4096 bits. This means that the SSH key can hardly be cracked by brute force.
The same command allows a file name to be passed for the key.
$ ssh-keygen -t rsa -b 4096 -f my-keyA passphrase can now also be assigned for even more security, but this is not absolutely necessary. If you want to use a passphrase for the SSH key, you can type in one and then confirm it. Otherwise, you can skip this option with hit Enter. We create a key pair at this point without additional passphrase.
That’s it: The key pair is created and is in the specified file. These can be opened with a text editor in the terminal with vi or nano, and with macOS with any editor to view the key pair, but nothing may be changed, even no blank lines may be inserted.
my-key
my-key.pubThe output is shown similar to this one.
ssh-rsa AAAAB3NzaC1yc2EAAADAQABACQCuA1tumTMG/sa7OpjxbuL5vz7R..
...
VOOpjavLDM0iZjWbRc3KeKuEIu9Lw== mike@thinkpad
The content of my-key.pub in abbreviated form are similar to this.
Bring a public SSH key to the server
Now there is the last step to store the public SSH key on the desired Server. The best way to do it is on the server with “ssh-copy-id”. Since the creation took place on the “control computer”, i.e. the laptop, the public key still has to be copied to the Server. First, you log in to the server and then store the key there. To do this, the necessary command in the terminal is as follows.
$ ssh-copy-id -i ~/.ssh/my-key mike@webserver.orgAlternatively, if you do not want to use “ssh-copy-id”, the contents of the local file ~/.ssh/my-key.pub can be copied to the Server in the file ~/.ssh/authorized_keys. To do this, run the command in the shell on the control computer.
$ cat ~/.ssh/my-key.pub | ssh mike@webserver.org "mkdir -p ~/.ssh && cat >> ~/.ssh/authorized_keys"
chmod 0600 ~/.ssh/authorized_keysAlternatively, the public SSH key can also be saved directly in the file authorized_keys via copy paste.
The private key my-key must remain secret, so do not place it on the server.
On Windows, OpenSSH can be deployed, under Settings – Apps and Features – Optional Features, or PuTTY (puttygen) is used.