This guide shows how to provide One-time Password (OTP) for 2FA 2-factor authentication with OPNsense TOTP and Google Authenticator. All OPNsense services can be used with the 2FA solution.
Step 1 – Add authentication server
To add a TOTP server, go to System ‣ Access ‣ Servers and click the plus (+) for Add server in the top right.
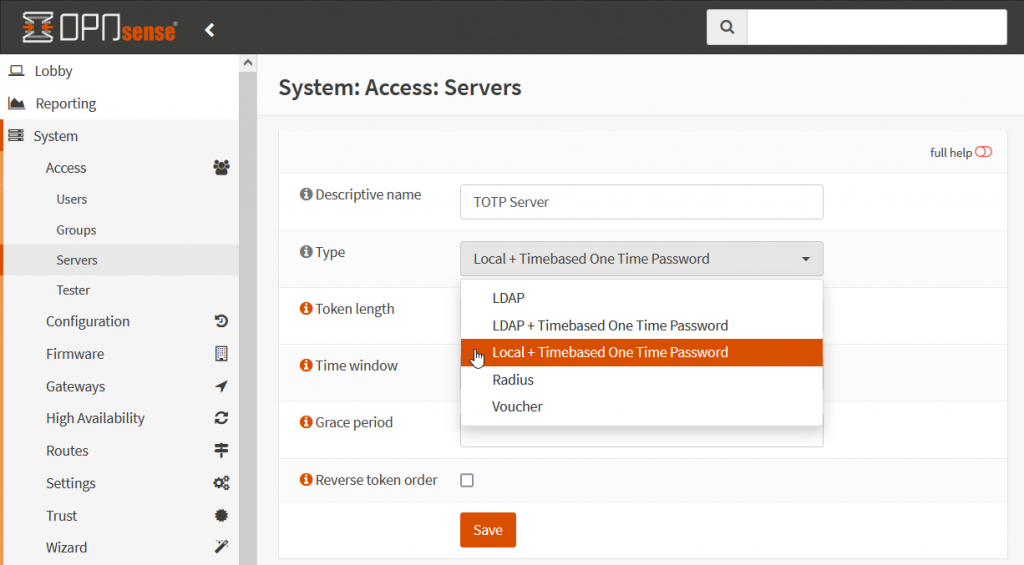
Select Type Local+Timebased One Time Password from drop-down list.
Step 2 – Add or change users
For this example, we’ll create a new OPNsense user for 2FA, go to System ‣ Access ‣ Users and click the plus (+) in the right corner.
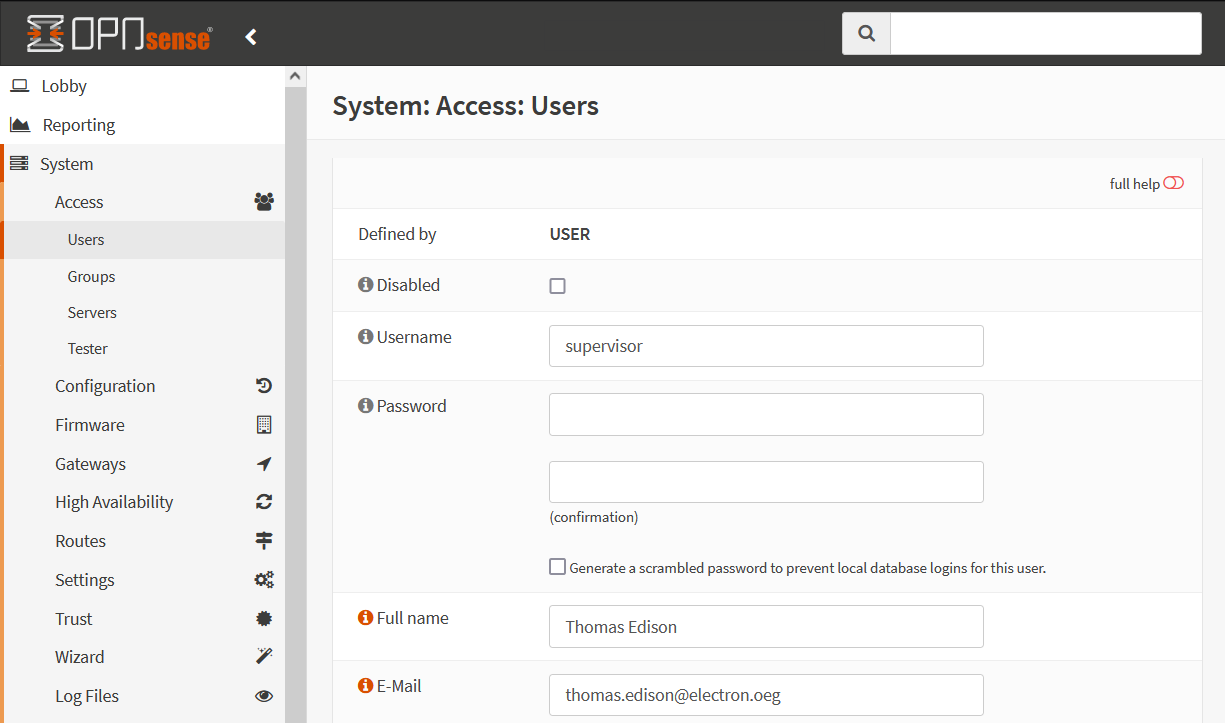
Enter a username and password and fill in the other fields, just like for any other user. Then left at OTP-seed click the checkbox at Generate new secret (160bit).
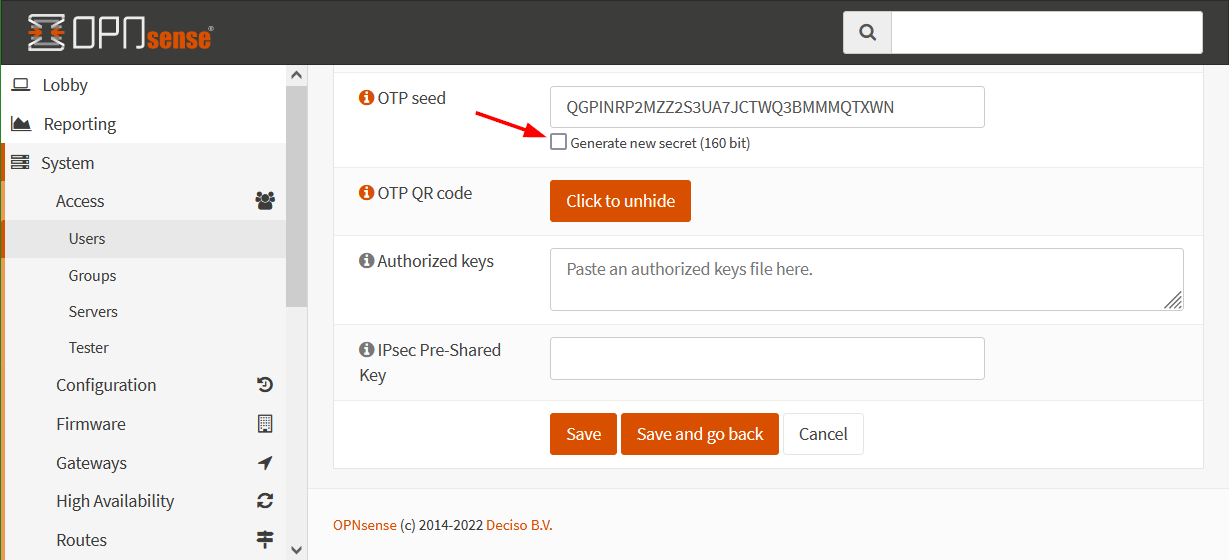
Then click the Save button.
Step 3 – Enable the authenticator for OTP seed
To activate the new OTP seed on the Google Authenticator, first open the user you just created again, click on the pencil icon, then on the Click to unhide button.
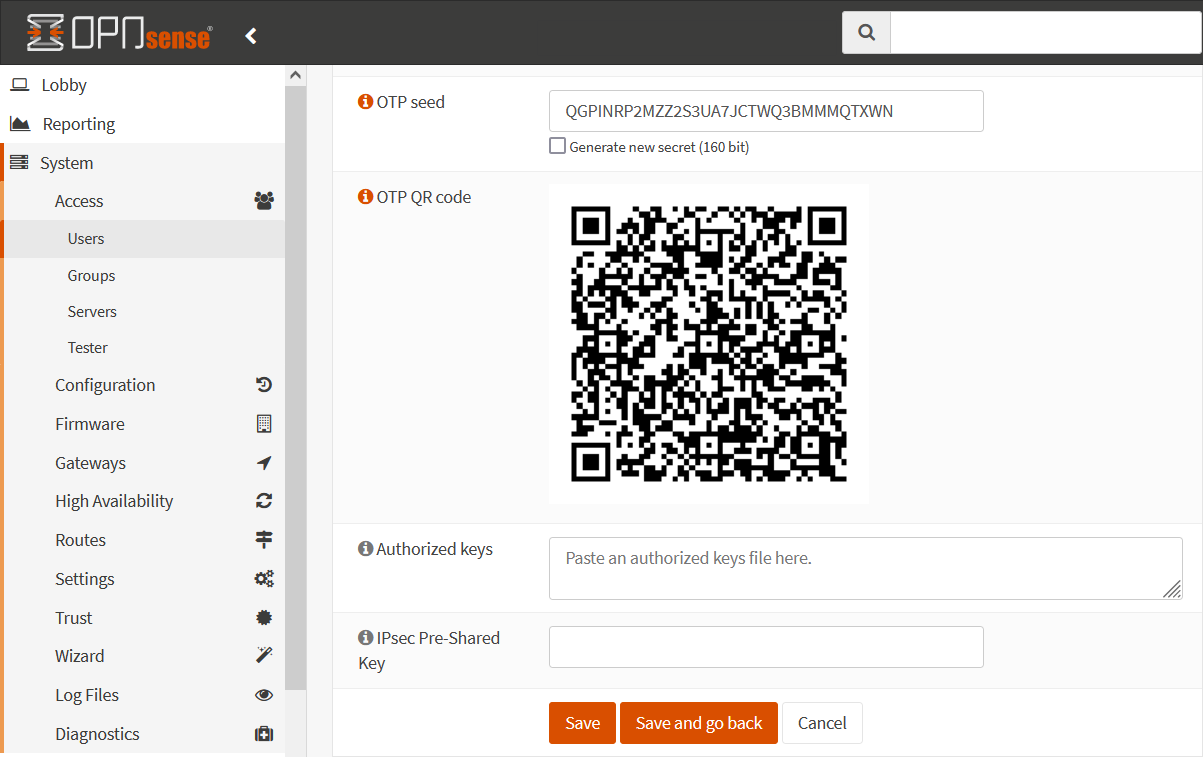
Be very careful with the seed or QR code as this is the only thing you need to calculate the token. KEEP YOUR SEED/QR CODE SAFE !
Step 4 – Activate authentication server
Now activate the authentication server and deactivate the local database, under System ‣ Settings ‣ Administration on Authentication – Server: click on TOTP Server.
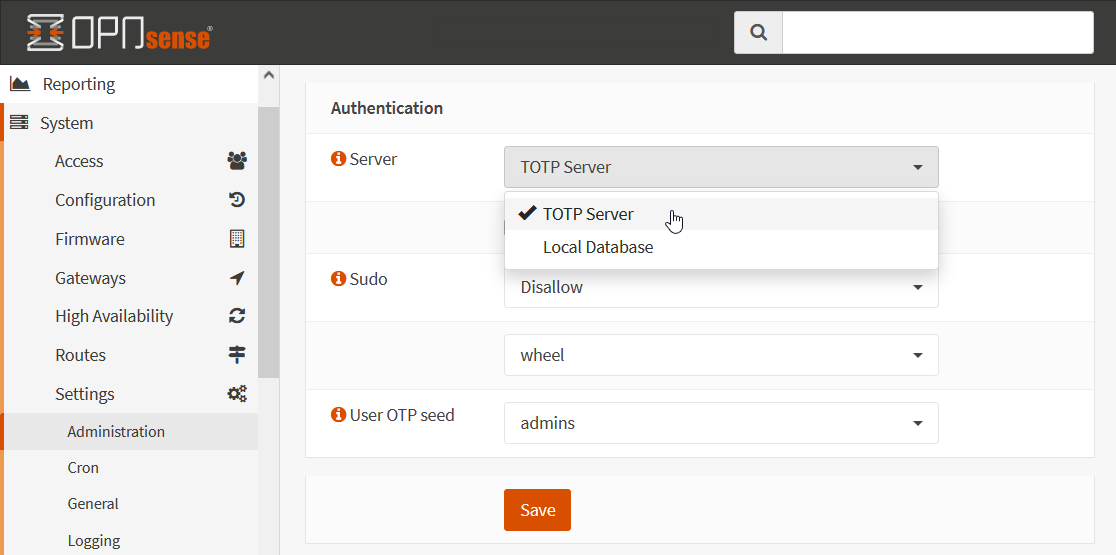
Do deactivate the Local Database and click the Save button.
Step 5 – Google Authenticator Installation
Open your platform’s App Store, such as iOS or Android, and search for Google Authenticator. Install the app on your device as usual.
Step 6 – Scan QR code
Now open the Google Authenticator app on your smartphone or tablet PC and select the option to scan the QR code, may with the + icon, alternatively the seed can be entered directly.
Testing OPNsense 2FA TOTP with Google
To test user OPNsense 2FA authentication, OPNsense offers a simple tester. This under System ‣ Access ‣ Tester.
Select the previously configured authentication server and enter the user name. The entry must be made in the form of token + password together in the password field.
The password field is used to enter both the token and password, ie. Password: 123456PASSWORD when using the default configuration. The OTP authentication server can also be configured to be used in reverse order like PASSWORD123456.
The next relevant post might also be helpful, see OpenVPN Connect using on iPhone and Android shows how to connect with OPNsense.