Install Midnight Commander in Synology DSM Terminal Shell
This post shows how to deploy Midnight Commander on a Synology NAS, the file manager for the file system in the Synology Shell via SSH. Midnight Commander, short mc is one of the most well-known console programs on Linux. Fortunately, you can easily add additional software repositories to the Synology NAS to install additional tools.
The Midnight Commander is not provided or managed by Synology itself, but can be retrieved from the SynoCommunity repository. The SynoCommunity offers free packages for Synology NAS devices.
How to add the SynoCommunity repository
From DSM you open the main menu with the icon at the top left, there you will find the Package Center.
By clicking on the icon Package Center to open this, then click the Settings button.
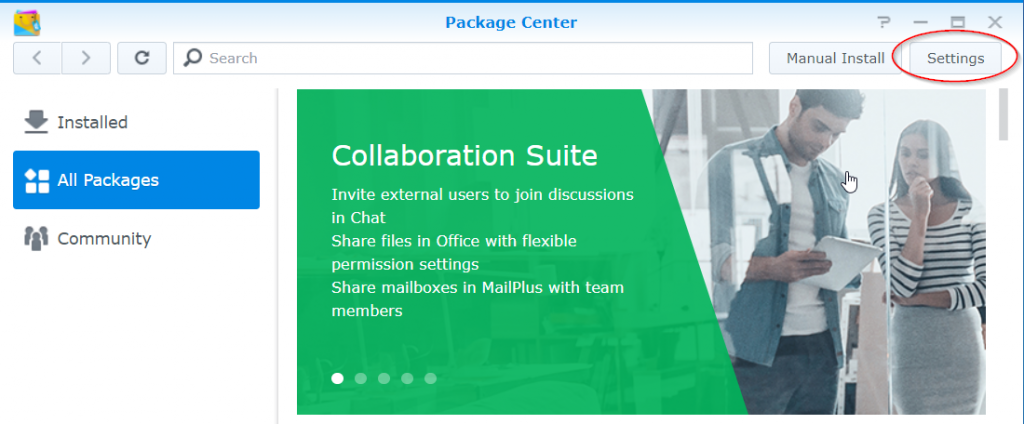
In the now opened General window under Trust Level, enable the Synology Inc. and trusted publishers option.
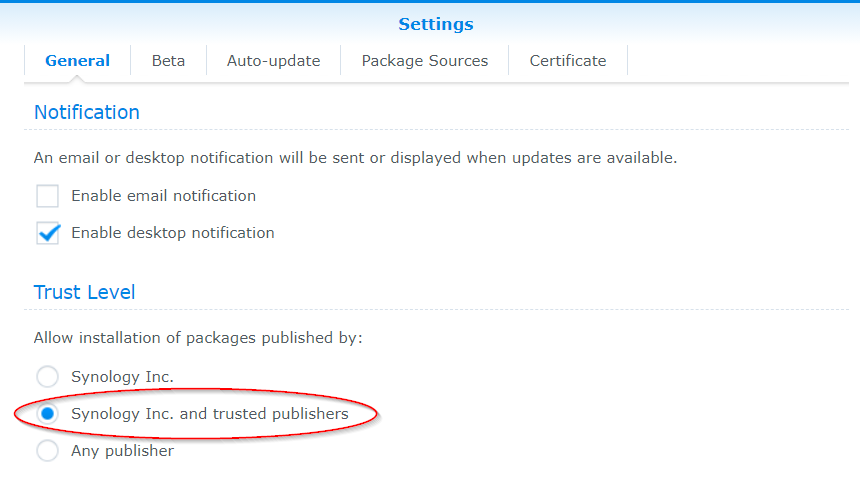
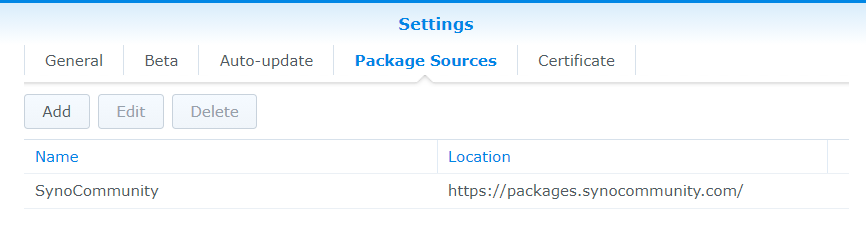
Then go to the Package Sources section.
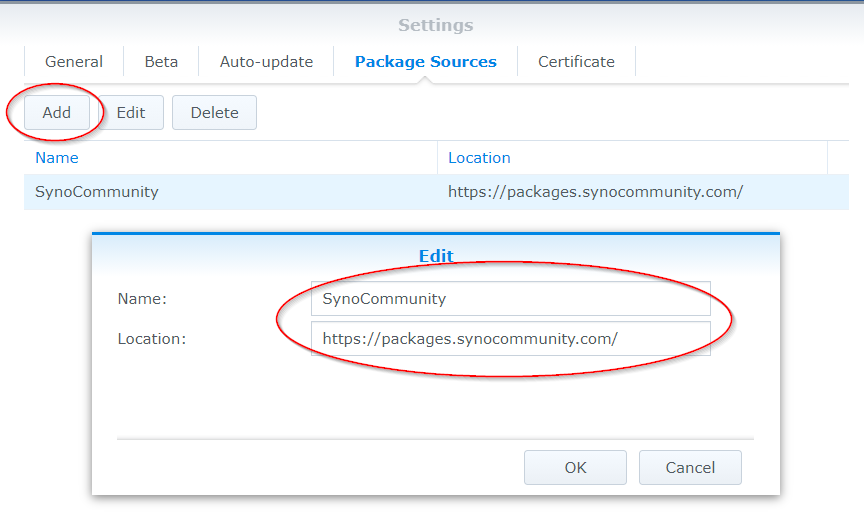
Click the Add button and insert the package source, enter SynoCommunity as the name, and insert the URL https://packages.synocommunity.com/ at location and click OK.
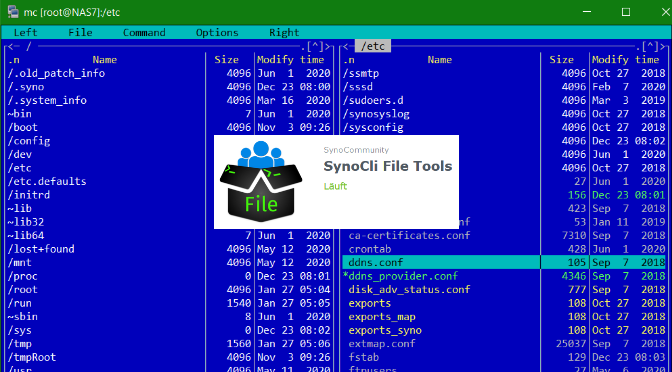
Packages can now be installed. The SynoCli File Tools package provides the following command-line utilities: less, tree, ncdu, jdupes, rhash, mc (midnight-commander), nano, file, detox, rmlint, rnm, pcre2, zstd. Nano used to be a separate package, but is now only available through the SynoCli File Tools package.

Now you can connect with a terminal like PuTTY to diskstation and run mc in the shell.
NAS7:/$ sudo mc
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
Password:Midnight Commander
Use sudo to run mc, after the admin password is entering the Midnight Commander is opened.
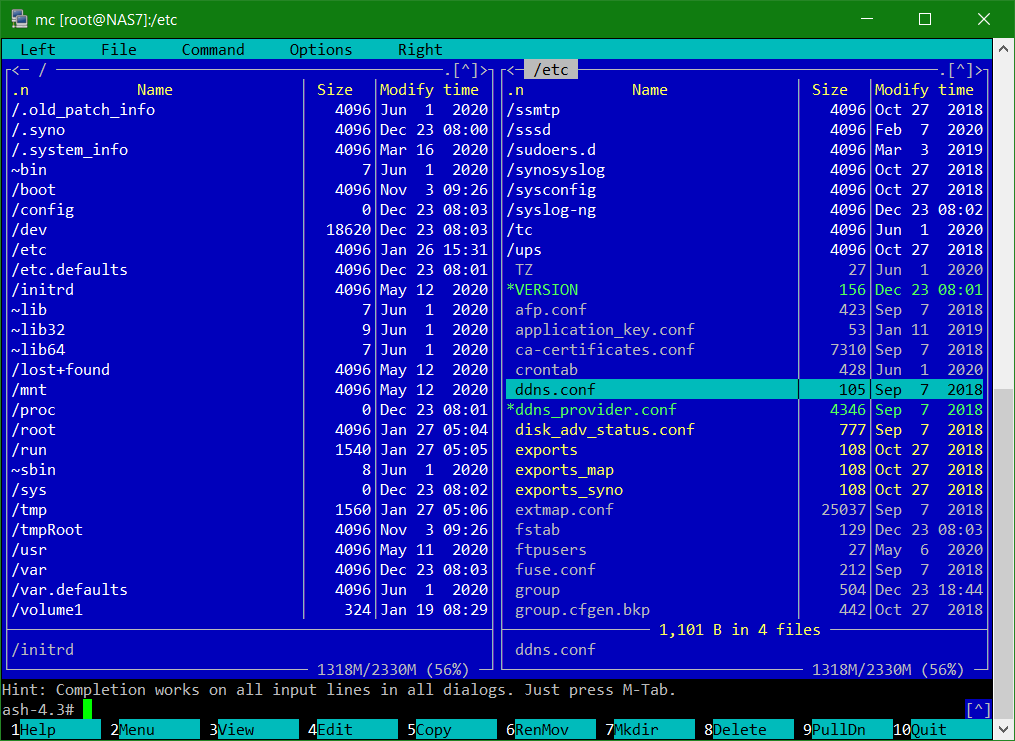
In the menu bar below, the functions of mc can be used via the F-keys or also with the mouse, such as Edit or Copy, with the cursor keys or the mouse you navigate in the window, press tab to switch to the other window, press F10 to leave Midnight Commander.
Remember, changes to system files require knowledge of the function and its effects.
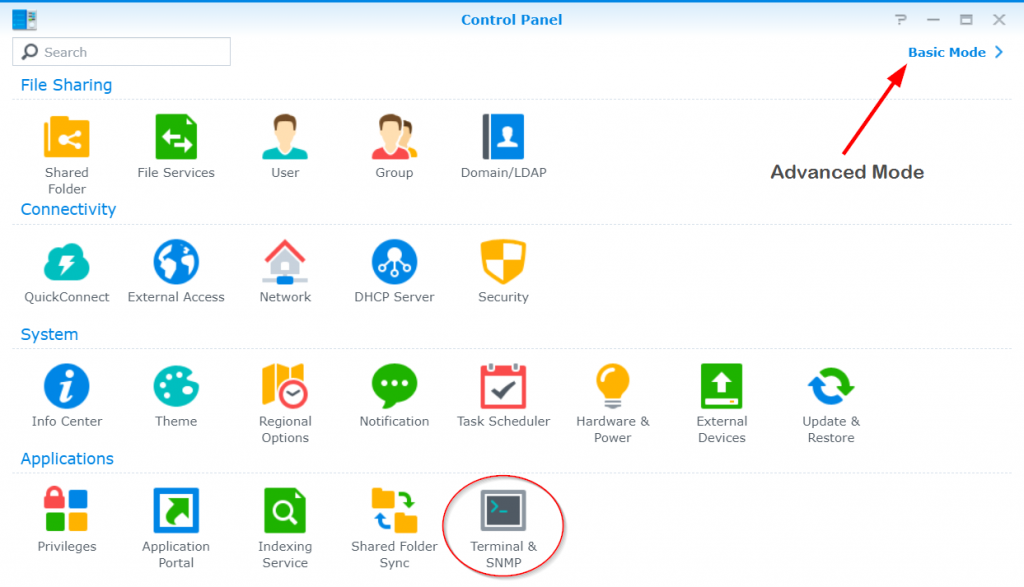
Enable Synology DSM SSH service
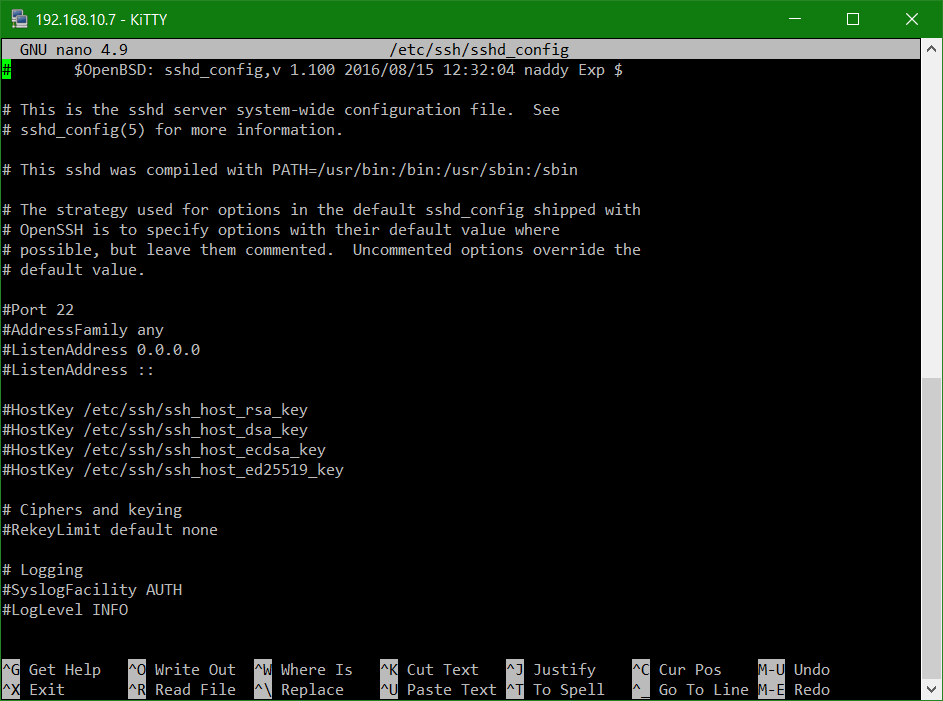
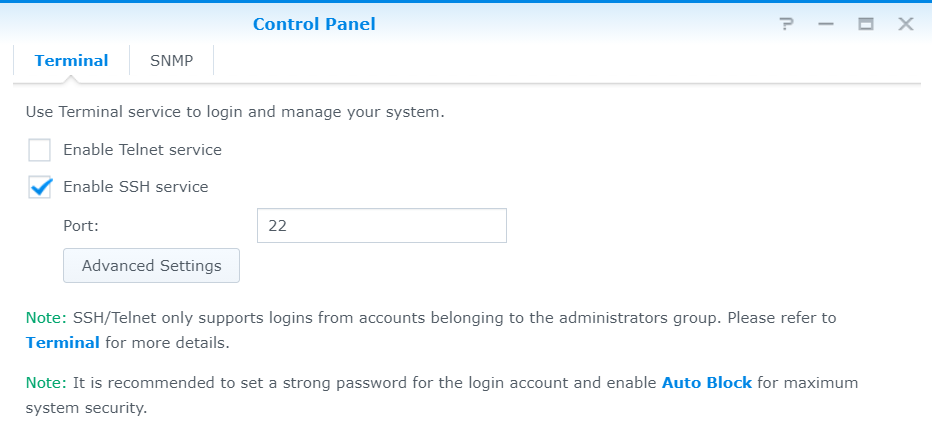
In order for the terminal to be accessible via SSH, the SSH service must be activated in the DSM Control Panel, under Terminal & SNMP, in order to make the Icon Terminal & SNMP visible, Advanced Mode is selected at the top right.
In the Terminal window, enable the SSH service option.
Next post on the same topic might be helpful, see in How to Install Nano on Synology NAS