Let’s understand Transport Layer Security TLS 1.2 and TLS 1.3 Windows TLS Protocols
Cyber attacks forces systems to more secured communication protocols to protect their assets and network from attacks. TLS plays a vital role in the implementation stack. With TLS is a critical security protocol that is used to encrypt communications between clients and servers. TLS 1.2 and TLS 1.3 are the two latest versions of the Transport Layer Security (TLS) protocol and offer many advantages over their previous versions. TLS 1.2 is the most widely used version of the TLS protocol, but TLS 1.3 is gaining popularity. System administrator should enable TLS 1.2 and TLS 1.3 on Windows Server to enhance the security of infrastructure.
Let’s understand Windows Transport Layer Security, TLS 1.2 and TLS 1.3 and what these TLS protocols offer more than their previous releases. Both TLS 1.2 and TLS 1.3 introduces new cryptographic suites that provide encreased security than the suites used in older TLS and SSL protocols. TLS 1.0 from 1999 and TLS 1.1 from 2006 have both been deprecated since March 2021. Both TLS 1.2 and TLS 1.3 are more resistant to man-in-the-middle attacks and simplify the handshake process, which makes it more difficult for attackers to eavesdrop on communications.
How to Enable TLS 1.2 on Windows Server
Microsoft provide TLS 1.3 protocol support only in Windows 11 and Windows Server 2022 and newer. No support will be provided for TLS 1.3 for Windows 10 and Windows Server 2019 and older. You can refer to the table below that shows the Microsoft Schannel Provider support of TLS protocol versions.
Windows Operating System Supported TLS Protocols:
| Windows OS | TLS 1.2 Client | TLS 1.2 Server | TLS 1.3 Client | TLS 1.3 Server |
|---|---|---|---|---|
| Windows Server 2008 with Service Pack 2 | Disabled | Disabled | Unsupported | Unsupported |
| Windows 7/Windows Server 2008 R2 | Disabled | Disabled | Unsupported | Unsupported |
| Windows 8/Windows Server 2012 | Enabled | Enabled | Unsupported | Unsupported |
| Windows 8.1/Windows Server 2012 R2 | Enabled | Enabled | Unsupported | Unsupported |
| Windows 10, version 1507 | Enabled | Enabled | Unsupported | Unsupported |
| Windows 10, version 1607/Windows Server 2016 Standard | Enabled | Enabled | Unsupported | Unsupported |
| Windows 10, version 1703 | Enabled | Enabled | Unsupported | Unsupported |
| Windows 10, version 1909/Windows Server 2019 | Enabled | Enabled | Experimental | Unsupported |
| Windows 10, version 2004 | Enabled | Enabled | Experimental | Unsupported |
| Windows 10, version 20H2-21H1-21H2 | Enabled | Enabled | Experimental | Unsupported |
| Windows Server 2022 | Enabled | Enabled | Enabled | Enabled |
| Windows 11 | Enabled | Enabled | Enabled | Enabled |
Enable TLS 1.2 Protocol using Windows Registry
Open up an command prompt as Administrator with hit the Windows+R keys and enter cmd and choose Run as administrator.
Now run the following commands to create the registry entries without to open the registry editor and do not having navigate to the key path.
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" /v "DisabledByDefault" /t REG_DWORD /d "0" /f
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" /v "Enabled" /t REG_DWORD /d "1" /f
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" /v "DisabledByDefault" /t REG_DWORD /d "0" /f
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" /v "Enabled" /t REG_DWORD /d "1" /fJust after a reboot the change is activated.
Enabling TLS 1.2 as default protocol WinHTTP
When an application specifies WINHTTP_OPTION_SECURE_PROTOCOLS, the system checks for the DefaultSecureProtocols registry entry and, if present, overrides the default protocols with the protocols specified in the registry entry. If the registry entry does not exist, WinHTTP uses the existing operating system settings for WINHTTP_OPTION_SECURE_PROTOCOLS HTTP. These WinHTTP defaults follow existing rules of precedence and are overridden by SCHANNEL disabled protocols and protocols set per application by WinHttpSetOption.
The DefaultSecureProtocols registry entry can be added as following :
REG ADD "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp" /v "DefaultSecureProtocols" /t REG_DWORD /d "2048" /fOn x64-based computers, DefaultSecureProtocols must also be added to the Wow6432Node path:
REG ADD "HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp" /v "DefaultSecureProtocols" /t REG_DWORD /d "2048" /fNote. the value 0x00000800 (hex 2048) means TLSv1.2.
Enable TLS 1.3 Protocol on Windows Server
Similar to above steps, on Windows 11 and newer, Windows Server 2022 and newer, create a DWORD (32-bit) set Enabled keys in the way below to enable TLS 1.3 with add the EnableHTTP3 key.
REG ADD "HKLM\SYSTEM\CurrentControlSet\Services\HTTP\Parameters" /v "EnableHTTP3" /t REG_DWORD /d "1" /fTLS 1.3 only supported in Windows 11 and Windows Server 2022.
Enable TLS 1.3 Protocol using PowerShell
Enable TLS 1.3 protocol on Windows Server using the simple procedure with ran the following PowerShell command as administrator.
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\services\HTTP\Parameters' -PropertyType 'DWORD' -Name 'EnableHttp3' -Value '1'How to Run Internet Options MMC-Console
Internet Explorer and many other web browsers can be configured by changing Internet Options settings. Although Internet Explorer uses all of these settings, other browsers, including Edge, don’t wholly rely on Internet Options for configuration. Microsoft Edge Chromium rendered browser settings can find under edge://settings
In Windows 10 and Windows 11 there is still the MMC-console module for Internet Properties, which can be opened directly with hit the Windows+R keys and raninetcpl.cpl
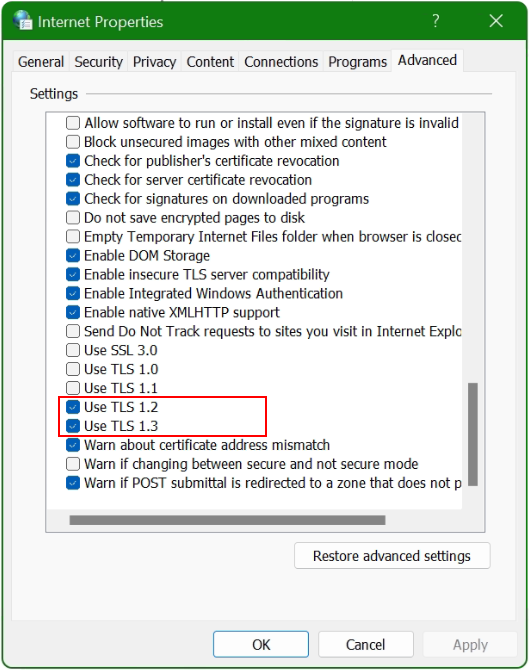
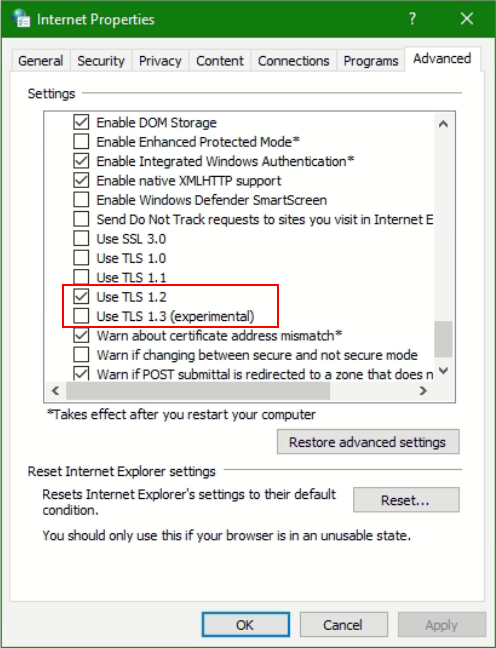
Windows 11 users can enable TLS v1.3 protocol in the advanced section of the internet options. By default, TLS v1.3 is system-wide enabled. Microsoft Edge start TLS 1.3 support from version 79.
Note. Windows 10 included an experimental implementation of TLS v1.3 with Windows 10 version 1909. By default TLS v1.3 is disabled system-wide, TLS 1.3 can by enabled for testing purposes.
if you want to know what are the cipher preferences of a established HTTPS connection, then the post here gives further assistance.
Conclusion
This post will learn you how to enable Windows TLS Protocols, TLS 1.2 and TLS 1.3 on your Windows operating systems to enhance the security of your infrastructure in a quick and simple way.