How to Test HTTPS and IMAPS connection using OpenSSL
OpenSSL can be used in many ways, so not only keys and certificates for SSL/TLS encrypted connections can be generated, but also their analysis and testing is possible.
This article shows how to perform the usage of OpenSSL for verification and analysis, when accessing web servers via TCP port 443 and STARTTLS over TCP 587 or IMAPS TCP 993 to mail server, which requires OpenSSL on the computer.
The free online service SSL Labs provide deep analysis of the configuration of any SSL web server that can be performed, the connection is performed with many different browsers and displayed, and which encryption has been achieved. The evaluation shows which encryption methods and key exchange methods have been used.

HTTPS Connection Test with OpenSSL
If individual tests are to be performed, the following examples show how to do this. An encrypted connection to unblog.ch is established and then the Web page is retrieved.
$ openssl s_client -connect unblog.ch:443 -showcertsIn a situation where an alternate port is used instead of the default port 443 for HTTPS, for example, 4443, the command is the same, with :4443 specifying the port number.
Retrieve certificate in RAW text
If you want to retrieve the public certificate of a web page in the RAW text, the certificate can be issued by the following command line.
$ openssl s_client -connect think.unblog.ch:443 -showcerts | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p'This command runs in a Linux terminal, in macOS terminal, in Git Bash or in a WSL session, the output between:
from: —–BEGIN CERTIFICATE—–
to —–END CERTIFICATE—–
-----BEGIN CERTIFICATE-----
MIIFajCCBFKgAwIBAgISAwYFPWKaEox8MgKHV5yqROeWMA0GCSqGSIb3DQEBCwUA
MEoxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MSMwIQYDVQQD
ExpMZXQncyBFbmNyeXB0IEF1dGhvcml0eSBYMzAeFw0yMDA3MTcwMzAyMTZaFw0y
...
-----END CERTIFICATE-----copy paste in Notepad and save as PEM/CER file (.cer).
By double-clicking on the public certificate saved in this way, it opens and appears on Windows as follows.
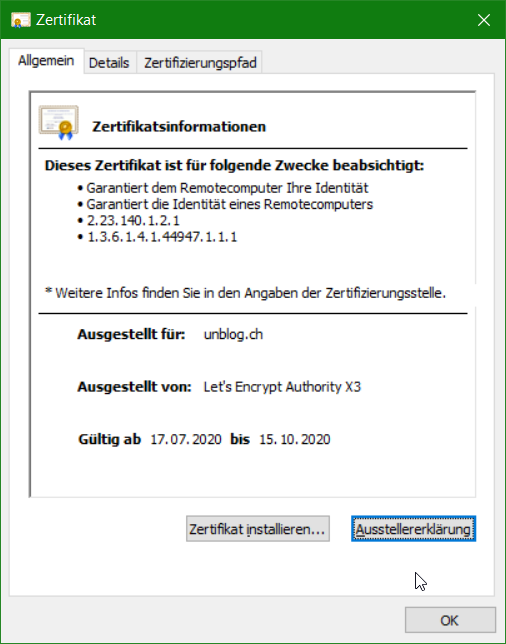
SMTPS Connection Test with OpenSSL
Use OpenSSL you can determine whether a mail server (MTA) offers encrypted STARTTLS connections, with the following command line.
$ openssl s_client -connect smtp-gw-246.server.com:587 -starttls smtpThe query displays the public certificate, then the encryption strength, the algorithm (SHA256), the TLS version (TLSv1.2), and cipher (ECDHE-RSA-AES256-GCM-SHA384) and other status information.
subject=CN = smtp-gw-246.server.com
issuer=C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 3441 bytes and written 480 bytes
Verification: OK
---
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN
SSL session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session ID: E1528C64C3CC7A9B28C4E1C2EA33EA0BEF1BACB6602B066351A49C705E192EB5
Session ID ctx:
Master Key: 573AB776B9954B51B7FE4908171752874EFCC3DE5F35ECC42AA5F04E48B736290DECC948DE252AD61188B5A94A8BAE9A
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 7200 (seconds)
TLS session ticket:
0000 - 0b 99 b3 3a 91 90 66 a8-86 8d 0e 41 8a 90 61 9e ...:.. Q....A.. A.IMAPS Connection Test use OpenSSL
Check IMAPs using OpenSSL in the command line, to perform the command line with IMAPS (SSL/TLS) connection can be checked over TCP port 993.
$ openssl s_client -crlf -connect imap.gmail.com:993The output then as here with CONNECT to imap.gmail.com via the SSL port 993 the raw output will displaying as shown in shortened way.
CONNECTED(00000174)
depth=1 C = US, O = Google Trust Services, CN = GTS CA 1O1
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 C = US, ST = California, L = Mountain View, O = Google LLC, CN = imap.gmail.com
verify return:1
---
Certificate chain
0 s:C = US, ST = California, L = Mountain View, O = Google LLC, CN = imap.gmail.com
i:C = US, O = Google Trust Services, CN = GTS CA 1O1
1 s:C = US, O = Google Trust Services, CN = GTS CA 1O1
i:OU = GlobalSign Root CA - R2, O = GlobalSign, CN = GlobalSign
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIExjCCA66gAwIBAgIQN1SnMAZHJA0IAAAAAFMdITANBgkqhkiG9w0BAQsFADBC
MQswCQYDVQQGEwJVUzEeMBwGA1UEChMVR29vZ2xlIFRydXN0IFNlcnZpY2VzMRMw
...
Post-Handshake New Session Ticket arrived:
SSL session:
Protocol : TLSv1.3
Cipher : TLS_AES_256_GCM_SHA384
Session ID: 6074E0D401DDD1E1DD5608CBC6F7CA4A2779A9AB4A9313732996D6C4DBD84BC68
Session ID ctx:
Resumption PSK:
...
read R BLOCK
* OK Gimap ready for requests from 12.34.56.78 t22mb67814ed
Q
DoneIf you want to continue here, you can try to authenticate on the IMAP server and query for new mails.
A NO [ALERT] Application-specific password required: https://support.google.com/accounts/answer/185833 (Failure)Gmail now responds with A NO [ALERT] which requires authentication security settings to have an application password because multi-factor authentication (MFA) is enabled.
* OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE LITERAL+ AUTH=PLAIN AUTH=LOGIN] Dovecot (Debian) ready.The following is a * OK with the output of the available functionalities (CAPABILITY). The IMAP Prompt is now waiting for input.
We can log in to our Dovecot IMAP server.
A login imap-user passwordThe login usually consists of the email address (imap-user) and a password.
After successful login, the output appears similar to this one.
A OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE SORT SORT=DISPLAY THREAD=REFERENCES THREAD=REFS THREAD=ORDEREDSUBJECT MULTIAPPEND URL-PARTIAL CATENATE UNSELECT CHILDREN NAMESPACE UIDPLUS LIST-EXTENDED I18NLEVEL=1 CONDSTORE QRESYNC ESEARCH ESORT SEARCHRES WITHIN CONTEXT=SEARCH LIST-STATUS BINARY MOVE SNIPPET=FUZZY LITERAL+ NOTIFY SPECIAL-USE QUOTA] Logged inNow we’re going to the IMAP inbox (INBOX).
A select INBOXThe output of select INBOX is similar to the following.
* FLAGS (\Answered \Flagged \Deleted \Seen \Draft $Forwarded)
* OK [PERMANENTFLAGS (\Answered \Flagged \Deleted \Seen \Draft $Forwarded \*)] Flags permitted.
* 3 EXISTS
* 0 RECENT
* OK [UNSEEN 3] First unseen.
* OK [UIDVALIDITY 1590737718] UIDs valid
* OK [UIDNEXT 12197] Predicted next UID
* OK [HIGHESTMODSEQ 39953] Highest
A OK [READ-WRITE] Select completed (0.001 + 0.000 secs).There are as seen 3 unread mails in the INBOX. From the first mail we open the header (starts with . dot).
. fetch 1 rfc822.headerThe output of . fetch 1 rfc822.header (the first 6 lines).
* 1 FETCH (RFC822.HEADER {3338}
Return-Path: <maxmuster@server.com>
Delivered-To: maxmuster@server.com
Received: from mail.server.com
by mail.server.com with LMTP
id sbn9BAzYQF9sJBACykIyCA
(envelope-from <maxmuster@server.com>)
..
. OK Fetch completed (0.001 + 0.000 secs).The first unread mail opens with . fetch 1 rfc822.text
. fetch 1 rfc822.textOutput of . fetch 1 then similar to here with my mail.
* 1 FETCH (RFC822. TEXT {596297}
--Apple-Mail-3B8B8770-2CCE-4083-B331-2E1EDAF97C84
Content type: text/plain;
charset=us-ascii
Content Transfer Encoding: 7bit
Good day.
Attached the PDF in the attachment.
Friendly greetings
--Apple-Mail-3B8C8770-2CCE-4083-B331-2E2EDBF97C94
Content type: application/pdf;
name="Doc-21.08.2020-10-36.pdf";
x-apple-part-url=CCDB9E0F-432F-2719-AE44-000259172822
Content disposition: inline;
filename="Doc-21.08.2020-10-36.pdf"
Content Transfer Encoding: base64
JVBERi0jLjMKJbe+7aoKMSAwIG9iago8PA0vVHlwZSAvQ2F0YWxvZwozUGFnZXMgMiAwIFIKPj4K
ZW5kc2JqCjIgMCBvYmoKPDwKL1R5cGUgL1BhZ2VzCi9LaWRzIFsgNCFxIFIgXQovQ291bnQgMQo+
...
. OK Fetch completed (0.003 + 0.034 secs).So this is a mail with PDF attachment, which is base64 encoded.
Enter Q will terminate the encrypted IMAP session.
Conclusion
OpenSSL as a versatile open-source toolkit offers numerous options, such as testing connections. Also including under Windows, as shown in this posting.



